“Stole $24 Million But Still Can’t Keep a Friend”
Credit to Author: BrianKrebs| Date: Wed, 16 Jan 2019 00:52:34 +0000
Unsettling new claims have emerged about Nicholas Truglia, a 21-year-old Manhattan resident accused of hijacking cell phone accounts to steal tens of millions of dollars in cryptocurrencies from victims. The lurid details, made public in a civil lawsuit filed this week by one of his alleged victims, paints a chilling picture of a man addicted to thievery and all its trappings. The documents suggest that Truglia stole from his father and even a dead man — all the while lamenting that his fabulous new wealth brought him nothing but misery.

The unflattering profile was laid out in a series of documents tied to a lawsuit lodged by Michael Terpin, a cryptocurrency investor who co-founded the first angel investor group for bitcoin enthusiasts in 2013. Terpin alleges that crooks stole almost $24 million worth of cryptocurrency after fraudulently executing a “SIM swap” on his mobile phone account at AT&T in early 2018. Terpin also is pursuing a $200 million civil lawsuit against AT&T in connection with the theft.
Authorities arrested Truglia on November 14, 2018 on suspicion of using SIM swaps to steal approximately $1 million worth of cryptocurrencies from a different Silicon Valley executive. But Terpin’s civil lawsuit (PDF) maintains that evidence was revealed at Truglia’s bail hearing that he had texted his father and multiple friends to brag about the $24 million hack on the day of Terpin’s theft, allegedly offering to take friends to the Super Bowl with “porn star escorts.”
Terpin’s lawsuit includes a large number of supporting documents, including an affidavit filed by Chris David, a 25-year-old New York City resident who claims to have been an acquaintance of Truglia’s until he began to unravel the source of his new friend’s overnight riches.
In his affidavit (PDF), David describes himself as a self-employed private jet broker who met Truglia in a fitness center attached to Truglia’s luxury apartment building. Truglia allegedly struck up a conversation about booking private jets with his cryptocurrency. When the two met again a few days later, David says Truglia showed him accounts on his mobile phone and computer indicating he had over $7 million in cash in a JP Morgan account and more than $12 million in various cryptocurrencies.
“At the same time, Nick showed me two thumb drives (Trezors),” David recounted. “One had over $40 million in cash value of various cryptos, and the other one had over $20 million cash value of various cryptos.”
David said Truglia initially explained his wealth by saying he’d made the money by mining cryptocurrencies, but that Truglia later would admit he stole the funds.
“Over the next few months, Nick and I socialized at nightclubs, local bars, the gym, and in his apartment playing video games,” David recounted. “Gradually, I got to know Nick. He does not have a job or visible means of support. His typical day is to get up late, go to the gym, eat at the deli across the street, play video games late into the night and he had no friends. Nick was an egotistical braggart about his life and wealth. For example, once at a crowded lounge, he said: ‘Chris, I have more money than all of the people here tonight.’”
David started documenting Truglia’s activities after he and several of his friends were arrested for allegedly stealing Truglia’s laptop, mobile phone and Trezor drive. That incident, recounted in this New York Post story and in David’s own testimony, indicates that Truglia later recanted the accusation and chalked it up to confusion resulting from a heavy night of drinking.
According to David, when Truglia wasn’t bragging about his wealth he was displaying it openly: He lived in a $6,000 per month apartment, wore a Rolex watch which he claimed cost $100,000, and boasted he was going to purchase a $250,000 McLaren sports car. David also said he recorded conversations with Truglia in which the latter admitted to stealing $24 million from Terpin.
David said he even witnessed Truglia attempting a SIM swap at a Times Square AT&T store in August 2018. Here’s David’s account of that hijack effort, which allegedly failed when Truglia declined to pay the target’s overdue phone bill:
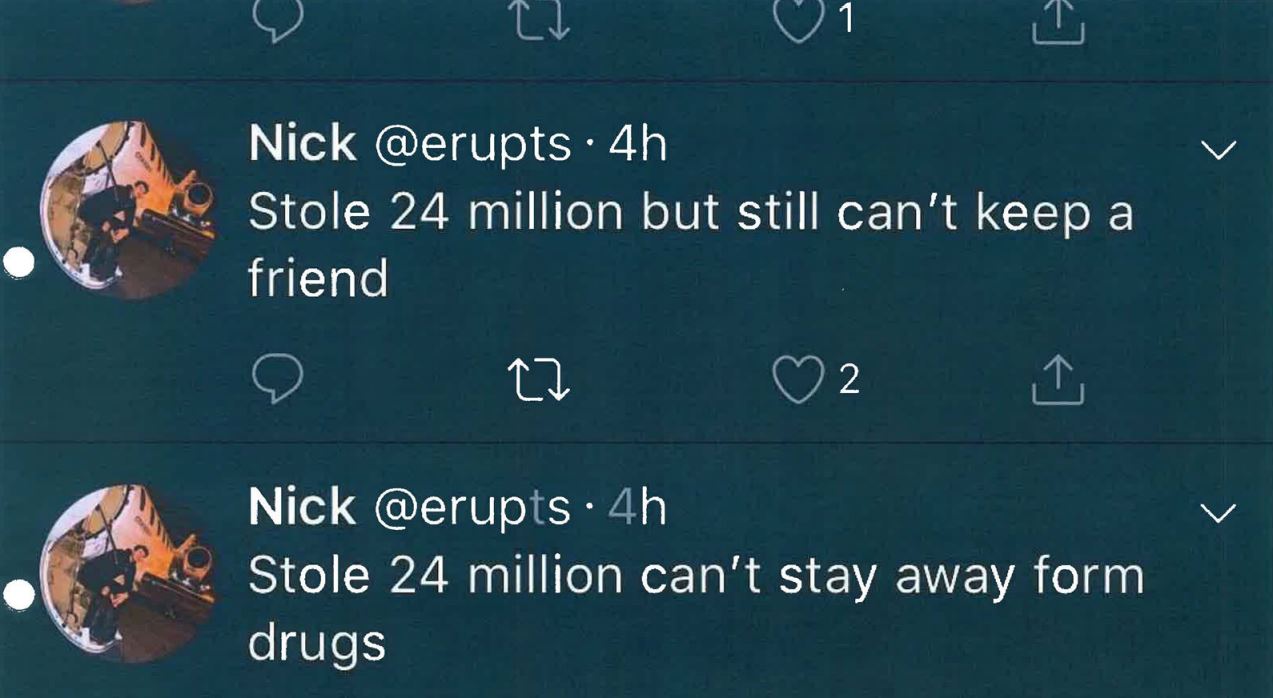
The affidavit states that later in the month David took screen shots of a now-defunct Twitter account that Truglia allegedly used (@erupts), which included six different messages about what the theft of $24 million had wrought.
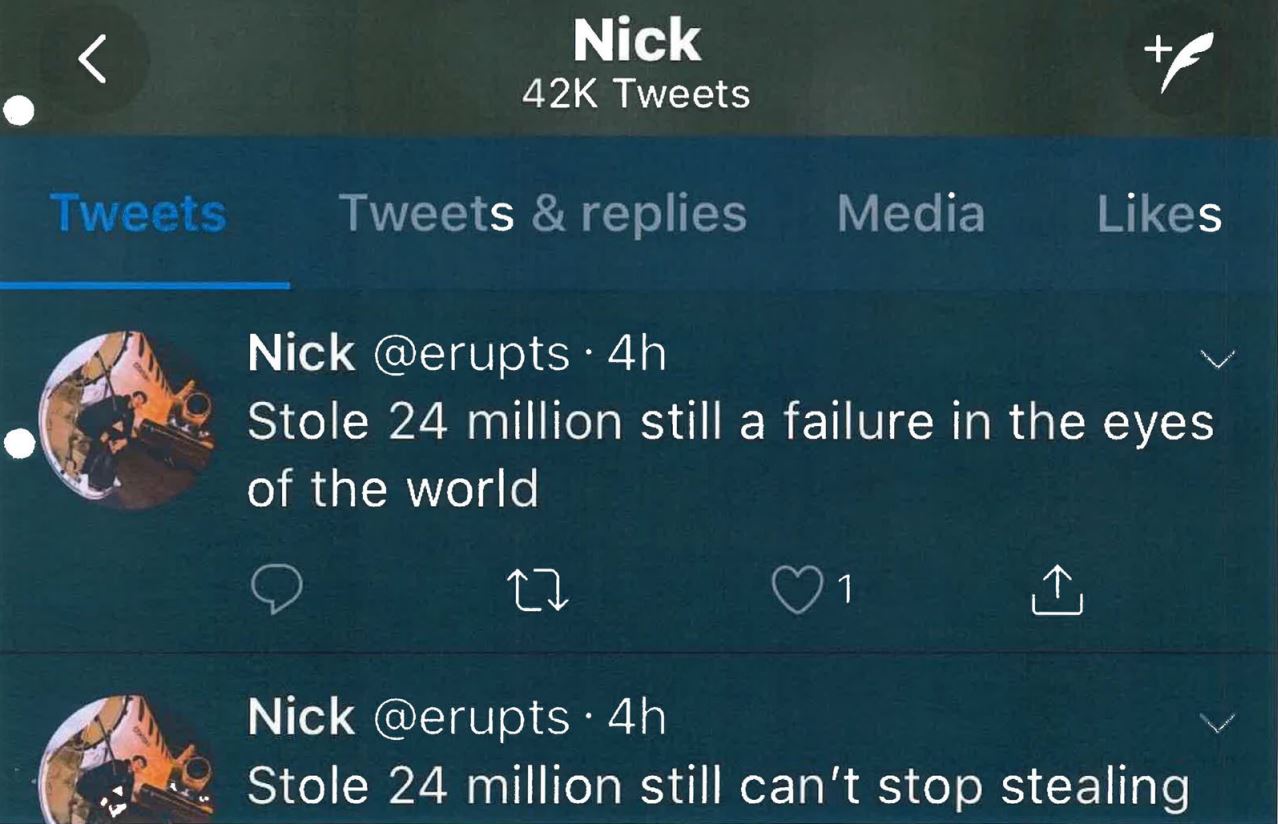
Tweets from the account @erupts, allegedly penned by Nicholas Truglia.
“Stole 24 million but still can’t keep a friend,” reads another tweet allegedly tied to Truglia’s account:
David says Truglia even acknowledged stealing $15,000 after hacking into his own father’s accounts. According to David, Truglia’s dad asked to be repaid, and that his son agreed to return the money — but in bitcoin. In the image below — which David claims was a screenshot he took of a mobile phone chat conversation between Truglia and his father — the elder expresses mystification and frustration about how to complete the transaction.
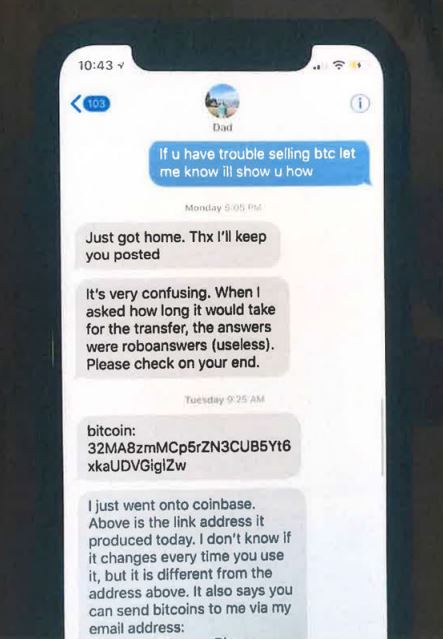
A screen shot David says he took of an alleged chat conversation between Truglia and his father regarding repayment of $15,000.
In the affidavit, David also testifies that he saw Truglia in possession of a fake New York State driver’s license which had the name and identifying information of a deceased man named Quentin Capobianco, but with Truglia’s photo on the license.
A copy of this phony drivers’ license was documented by investigators with the Regional Enforcement Allied Computer Team, or REACT — a task force in Santa Clara, Calif. that is almost singularly focused on tracking down criminals who use unauthorized SIM swaps to steal virtual currencies (for a deep dive into the workings of the REACT Task Force, see my November 2018 story, Busting SIM Swappers and SIM Swap Myths).

David said he took this photograph of a license Truglia had in his possession; the license includes Truglia’s photograph but the information of a dead man that Truglia allegedly SIM swapped.
That REACT Task Force investigation report (PDF) was included in Terpin’s lawsuit, and it lays out how detectives tied Truglia to SIM swaps that allegedly gave him access to Capobianco’s accounts at Coinbase, a virtual currency trading and purchasing platform.
David testified that despite Truglia’s ill-gotten riches, he was constantly borrowing small amounts of cash and was otherwise tight with his money. Much like David’s testimony, a related memo (PDF) filed by REACT Detective Caleb Tuttle suggests that Truglia was in the process of being evicted from his pricey Manhattan apartment because he refused to pay his rent.

A snippet from a memo filed about Truglia by REACT Task Force Detective Caleb Tuttle.
Truglia is currently being held by Santa Clara authorities on a $1.4 million bond. His next court date is April 10. Neither Truglia nor his attorney could be immediately reached for comment. Members of the REACT Task Force declined to comment for this story.
A SIM card is the tiny, removable chip in a mobile device that allows it to connect to the provider’s network. Customers can legitimately request a SIM swap when their existing SIM card has been damaged, or when they are switching to a different phone that requires a SIM card of another size.
But SIM swaps are frequently abused by scam artists who trick mobile providers into tying a target’s service to a new SIM card and mobile phone that the attackers control. Unauthorized SIM swaps often are perpetrated by fraudsters who have already stolen or phished a target’s password, as many banks and online services rely on text messages to send users a one-time code that needs to be entered in addition to a password for online authentication. However, many online services let customers reset their password merely by using their mobile phones.
All four major wireless carriers — AT&T, Sprint, T-Mobile and Verizon — let customers add security against SIM swaps and related schemes by setting a PIN that needs to be provided over the phone or in person at a store before account changes should be made. But these security features can be bypassed by incompetent or corrupt mobile store employees.
For more on ways to minimize your chances of becoming the next SIM swapping victim, check out the “What Can You Do?” section at the conclusion of this story.
