‘Fleeceware’ apps overcharge users for basic app functionality
Credit to Author: Jagadeesh Chandraiah| Date: Wed, 25 Sep 2019 14:01:49 +0000
SophosLabs have discovered a collection of Android apps on Google’s Play Market whose sole purpose appears to be to severely overcharge users for mobile apps that provide very simple functionality available on low-cost or free apps.
The app developers take advantage of a business model available within the Play Market ecosystem in which users can download and use the apps at no charge for a short trial period. When the trial expires, if the user who downloads and installs one of these apps hasn’t both uninstalled the application and informed the developer that they do not wish to continue to use the app, the app developer charges the user.
In the case of a normal app, this might cost only a few dollars; But the publishers or developers of the apps described in this post routinely charge users hundreds of dollars (or Euros, depending on the geographic region in which the user resides).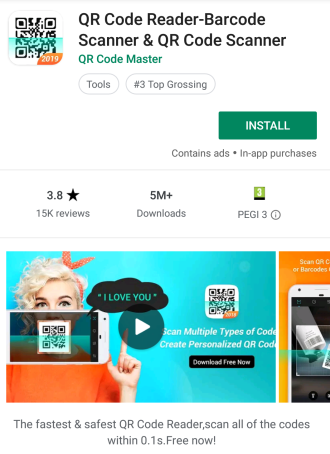 The apps themselves do not appear to be malicious or contain malicious code; Some of these apps may even have useful (if redundant) functionality. However, it’s hard to imagine that anyone who is charged hundreds of dollars for a simple barcode reader or photo filter would consider such an expense “potentially unwanted” – nobody wants that.
The apps themselves do not appear to be malicious or contain malicious code; Some of these apps may even have useful (if redundant) functionality. However, it’s hard to imagine that anyone who is charged hundreds of dollars for a simple barcode reader or photo filter would consider such an expense “potentially unwanted” – nobody wants that.
Because these apps exist in a categorical grey area that isn’t overtly malware, and isn’t a potentially unwanted app (PUA), we’ve coined the term fleeceware, because their defining characteristic is that they overcharge users for functionality that’s widely available in free or low-cost apps.
We reached out to representatives of Google’s Play Market to find out whether the terms and conditions under which these apps are sold violate any of Google’s public or internal policies.

We have not received a response from Google representatives about whether high-value monthly subscriptions to apps with very basic functionality violates their in-app purchasing policies. Last week, after Sophos had brought this purchasing behavior to their attention and sent along a list of 15 apps engaged in this practice, a Google representative told us the company had decided to pull some from their store. By our count, 14 of the 15 apps we informed Google about have been removed. A subsequent search revealed another batch of apps, with even higher download counts than the first, still available on the Play Market.
We encourage Google to do more to tighten up their policies that, currently, do not explicitly prohibit app developers from taking advantage of this in-app purchasing loophole. Customers who experience buyer’s remorse may have no recourse to ask for refunds after a few days. If you aren’t very actively monitoring your credit card for charges like this, you might not notice until the window for refunds has closed.
The fleeceware business model
Because the apps themselves aren’t engaging in any kind of traditionally malicious activity, they skirt the rules that would otherwise make it easy for Google to justify removing them from the Play Market. Their developers also seem to be very good at staying under the radar from security vendors. Even so, there are other characteristics of these apps that make them less-than-desirable.
These applications are, fundamentally, simple. We’ve observed tools like QR or barcode readers, calculators, tools to make animated GIFs, or photo editors. In most cases, there are free alternatives from well known vendors already available on the Play Market.
![]() When you run any of these apps, the app prompts the user to sign up for a very short free trial period, usually 3 days, through an interface within the app itself. The app makers require you to sign up with payment information before you can run the app, and many users fail to understand the requirement that, in order to drop out of the trial, they have to explicitly tell the developer that they are cancelling the trial period.
When you run any of these apps, the app prompts the user to sign up for a very short free trial period, usually 3 days, through an interface within the app itself. The app makers require you to sign up with payment information before you can run the app, and many users fail to understand the requirement that, in order to drop out of the trial, they have to explicitly tell the developer that they are cancelling the trial period.
Many simply forget to do so, or think that uninstalling the app constitutes a cancellation. But the app developers don’t see it that way.
In many reviews for fleeceware apps, users report that they failed to unsubscribe from the trial period, and get charged very high amounts of money. In the case of one QR code reader app, the developer charges users €104.99 after 72 hours. The makers of an app called Professional GIF Maker charge users €214.99 when the trial ends. We haven’t seen apps sold at this price before.
 It’s a business model that walks a fine ethical line, but it is apparently successful. Some percentage of users will fail to cancel the trial, even if they intend to do so, and the app makers earn their keep on the backs of users who forget to unsubscribe, or ask for a refund within the short window in which they can do so.
It’s a business model that walks a fine ethical line, but it is apparently successful. Some percentage of users will fail to cancel the trial, even if they intend to do so, and the app makers earn their keep on the backs of users who forget to unsubscribe, or ask for a refund within the short window in which they can do so.
With millions of installations, in some cases, if even a small percentage of users forgets to cancel their subscription before the trial period lapses, app creators can make significant money.
 App users see trial notifications like this one when they launch the apps that engage in this practice for the first time. People who sign up for the trial are required to provide payment information the first time they launch the app using Google’s in-app payments.
App users see trial notifications like this one when they launch the apps that engage in this practice for the first time. People who sign up for the trial are required to provide payment information the first time they launch the app using Google’s in-app payments.
Of course they can “cancel anytime” but this is a bit pricier than, say, a typical magazine subscription. Once you’ve been charged, there is hardly any recourse to get your money back.  Google Play Market actually permits these types of transactions because they follow the rules for in-app purchases. While they are clearly consumer-hostile, the apps are not otherwise malicious, and they do actually perform the function they claim to be able to do.
Google Play Market actually permits these types of transactions because they follow the rules for in-app purchases. While they are clearly consumer-hostile, the apps are not otherwise malicious, and they do actually perform the function they claim to be able to do.
 While consumers are free to purchase anything they like, we don’t think an app which generates an animated GIF image should cost hundreds of Euros or dollars. And in some cases, the publisher isn’t going to charge those users only one time: Several of these fleeceware apps inform users that they will be charged every month until the user cancels their subscription.
While consumers are free to purchase anything they like, we don’t think an app which generates an animated GIF image should cost hundreds of Euros or dollars. And in some cases, the publisher isn’t going to charge those users only one time: Several of these fleeceware apps inform users that they will be charged every month until the user cancels their subscription.
This is a breakdown of some of the fleeceware applications that we identified on Google’s Play Market. As we mentioned previously, 14 other apps that engaged in a similar business practice have subsequently been pulled from the Play Market by Google representatives after we inquired about the business model. The ones listed below are still available, so we have refrained from linking directly to them.
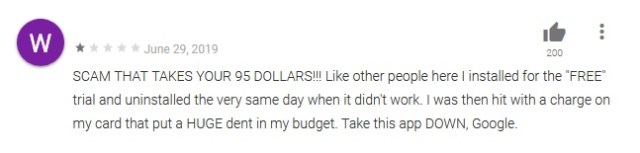
Users’ fleeceware fury
From the user reviews on the Play Market store, it’s clear that many users who installed these apps and were subsequently charged extortionate fees are understandably furious. Users indicated that they were charged different amounts based on their geographic region. Some people are asking Google to take these apps down, and some want get a refund.
Google addresses concerns
Google polices the apps that they publish on their online store for outright malicious activity and fraud. But these applications evaded Google’s attention by staying on the razor’s edge of legality, and exploited the fact that most people avoid reading fine print.
Worse, these apps are not even particularly good, unique, or effective. The publishers engaging in this business practice just offer their versions of apps that are widely used and already exist (in some cases, for free) from far more reputable vendors. For example, Sophos also has a QR code reader in our Sophos Mobile security application.
Tools like these are certainly useful, but not hundreds-of-dollars (or euros) -per-month useful. If there was ever a time to say so, caveat emptor!