Who’s In Your Online Shopping Cart?
Credit to Author: BrianKrebs| Date: Sun, 04 Nov 2018 19:10:06 +0000
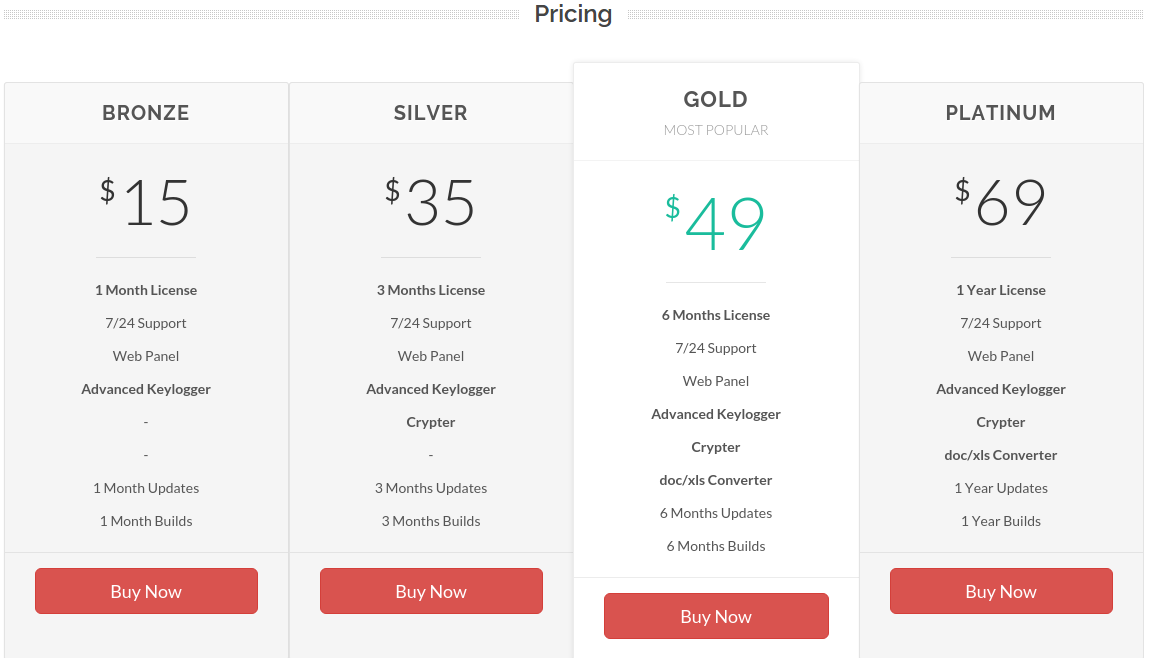
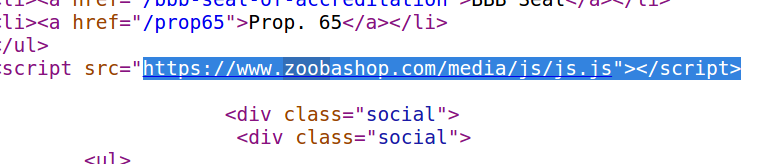
Crooks who hack online merchants to steal payment card data are constantly coming up with crafty ways to hide their malicious code on Web sites. In Internet ages past, this often meant obfuscating it as giant blobs of gibberish text that is obvious even to the untrained eye. These days, a compromised e-commerce site is more likely to be seeded with a tiny snippet of code that invokes a hostile domain which appears harmless or that is virtually indistinguishable from the hacked site’s own domain.
Read More