Romance scams costlier than ever: 10 percent of victims lose $10,000 or more
A Malwarebytes survey has found 66 percent of people were targeted by a romance scam, with 10 percent of victims losing $10,000 or more.
Read MoreRSS Reader for Computer Security Articles
A Malwarebytes survey has found 66 percent of people were targeted by a romance scam, with 10 percent of victims losing $10,000 or more.
Read MoreMalwarebytes is simplifying your security and privacy with the release of our new Personal Data Remover.
Read MoreCredit to Author: Takeshi Numoto| Date: Tue, 24 Sep 2024 14:00:00 +0000
At Microsoft, we have commitments to ensuring Trustworthy AI and are building industry-leading supporting technology. Our commitments and capabilities go hand in hand to make sure our customers and developers are protected at every layer. Building on our commitments, today we are announcing new product capabilities to strengthen the security, safety and privacy of AI systems.
The post Microsoft Trustworthy AI: Unlocking human potential starts with trust appeared first on Microsoft Security Blog.
Read More
Credit to Author: Vittoria Elliott| Date: Tue, 24 Sep 2024 11:30:00 +0000
The US government says outlets like RT work closely with Russian intelligence, and platforms have removed or banned their content. But they’re still influential all around the world.
Read MoreCredit to Author: Charlie Bell| Date: Mon, 23 Sep 2024 15:00:00 +0000
Since the Secure Future Initiative (SFI) began, we’ve dedicated the equivalent of 34,000 full-time engineers to SFI—making it the largest cybersecurity engineering effort in history. And now, we’re sharing key updates and milestones from the first SFI Progress Report.
The post Securing our future: September 2024 progress update on Microsoft’s Secure Future Initiative (SFI) appeared first on Microsoft Security Blog.
Read More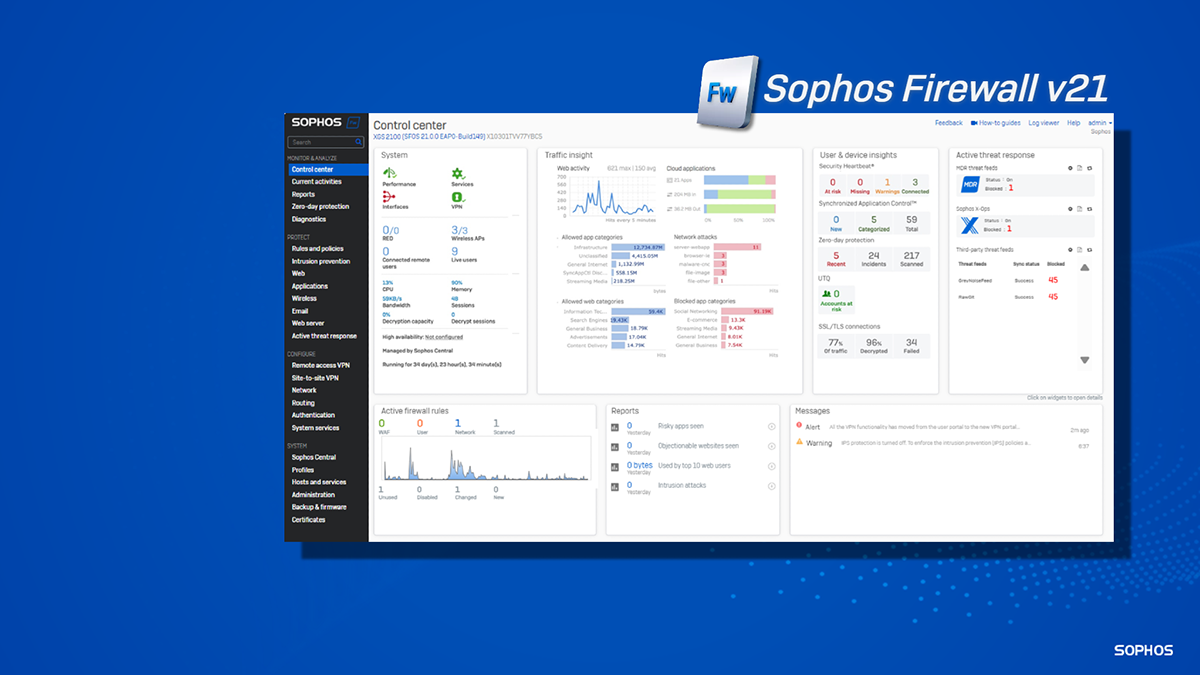
Credit to Author: Chris McCormack| Date: Mon, 23 Sep 2024 19:01:16 +0000
How to make the most of the new features in Sophos Firewall v21.
Read MoreA background check service called MC2 Data has leaked information of over 100 million US citizens in an unprotected online database.
Read MoreCredit to Author: Benjamin Lim| Date: Thu, 19 Sep 2024 16:00:00 +0000
Join us in November 2024 in Chicago for Microsoft Ignite to connect with industry leaders and learn about our newest solutions and innovations.
The post Join us at Microsoft Ignite 2024 and learn to build a security-first culture with AI appeared first on Microsoft Security Blog.
Read More