Crypto Mining Service Coinhive to Call it Quits
Credit to Author: BrianKrebs| Date: Wed, 27 Feb 2019 23:19:28 +0000
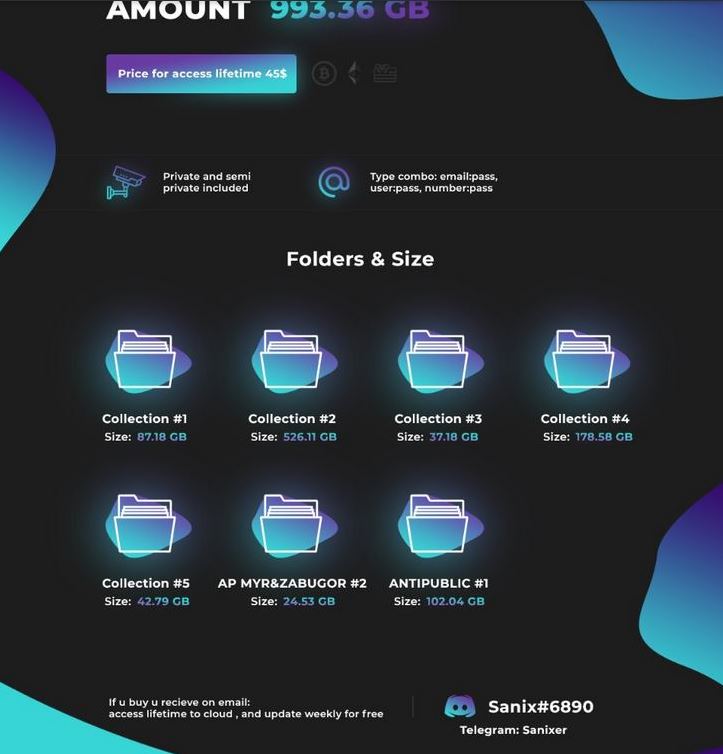
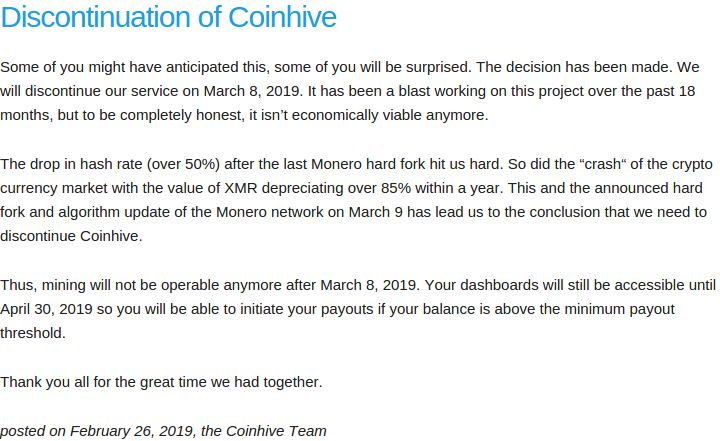
Roughly one year ago, KrebsOnSecurity published a lengthy investigation into the individuals behind Coinhive[.]com, a cryptocurrency mining service that has been heavily abused to force hacked Web sites to mine virtual currency. On Tuesday, Coinhive announced plans to pull the plug on the project early next month.
Read More