Tourists Give Themselves Away by Looking Up. So Do Most Network Intruders.

Credit to Author: BrianKrebs| Date: Tue, 22 Aug 2023 17:45:28 +0000
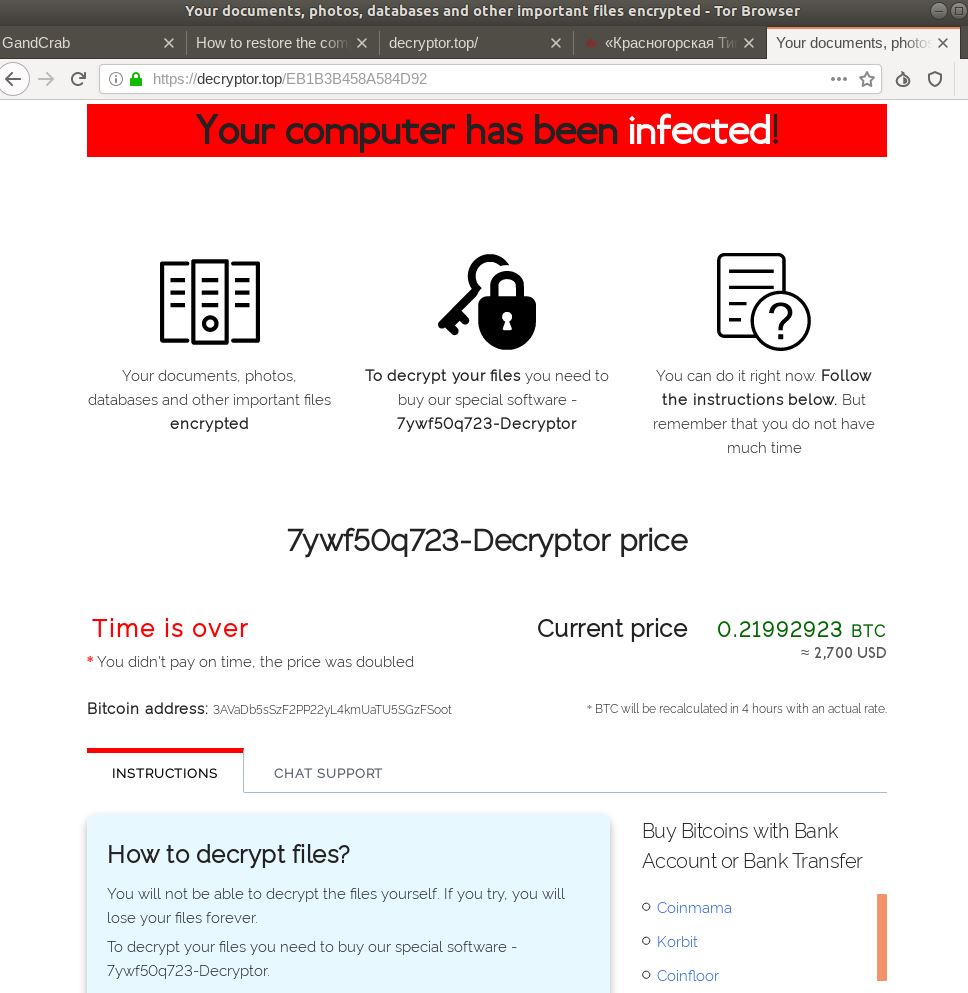
In large metropolitan areas, tourists are often easy to spot because they’re far more inclined than locals to gaze upward at the surrounding skyscrapers. Security experts say this same tourist dynamic is a dead giveaway in virtually all computer intrusions that lead to devastating attacks like ransomware, and that more organizations should set simple virtual tripwires that sound the alarm when authorized users and devices are spotted exhibiting this behavior.
Read More