Persistence in the Shadows: A Study of Zephyr Miner Exploiting System Services
Credit to Author: Rayapati Lakshmi Prasanna Sai| Date: Mon, 02 Dec 2024 15:15:15 +0000

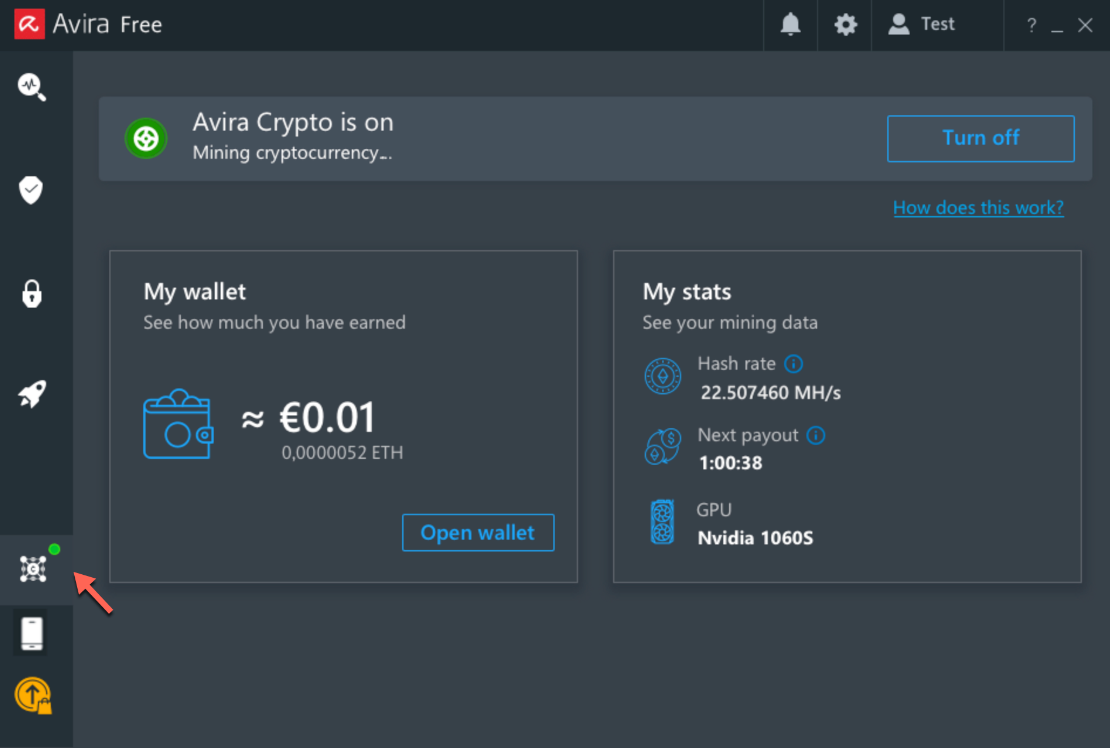
Crypto Mining Crypto mining is the process by which individuals or organizations use computer power to solve complex…
The post Persistence in the Shadows: A Study of Zephyr Miner Exploiting System Services appeared first on Quick Heal Blog.
Read More