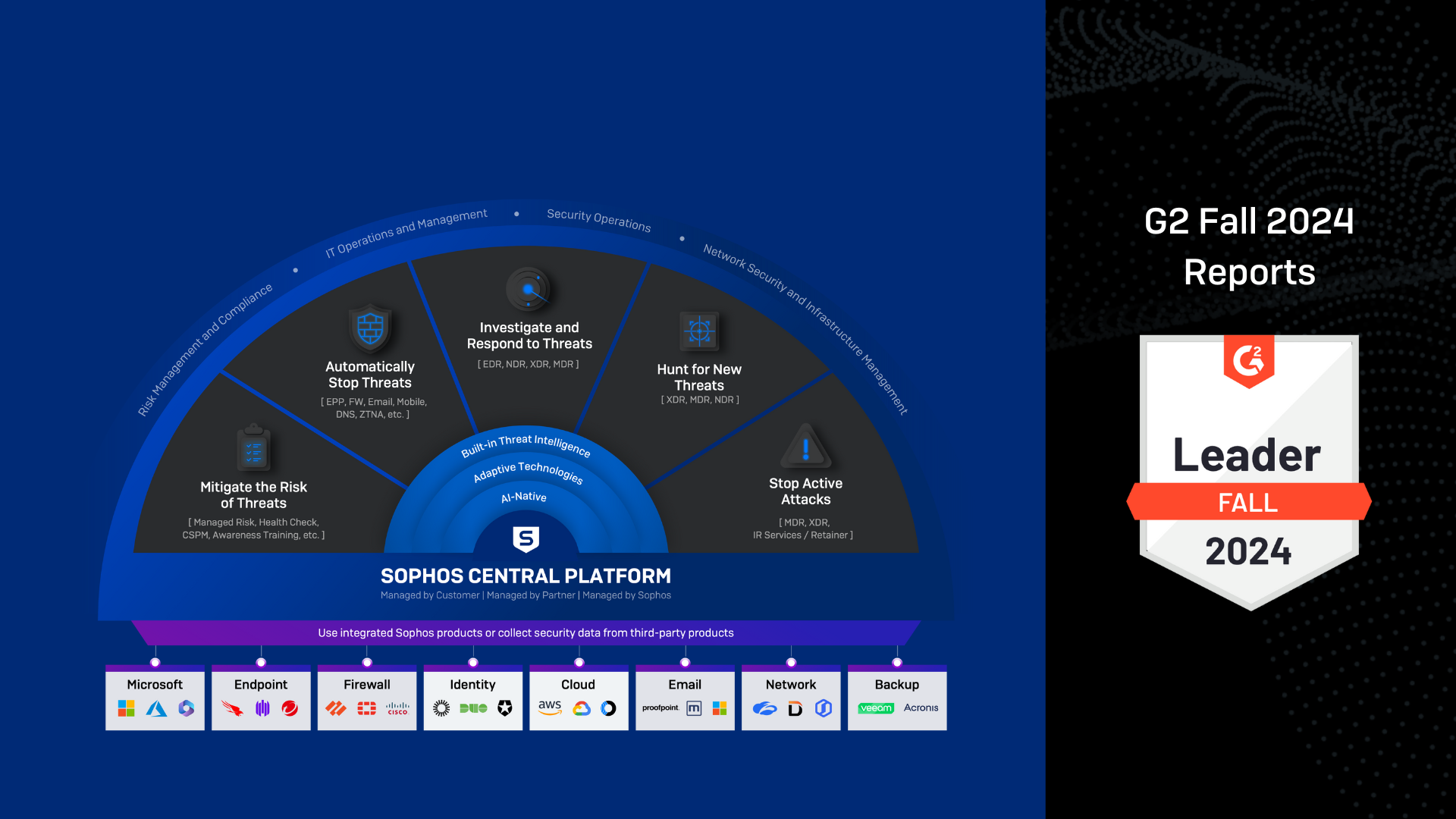
Sophos ranked #1 overall for Firewall, MDR, and EDR in the G2 Winter 2025 Reports

Credit to Author: rajansanhotra| Date: Wed, 18 Dec 2024 10:21:54 +0000
Sophos was also ranked the #1 solution in 36 individual reports spanning the Antivirus, EDR, Endpoint Protection Suites, XDR, Firewall, and MDR markets.
Read More