Uber, Rockstar fall to social engineering attacks; and you?

Credit to Author: Chester Wisniewski| Date: Thu, 22 Sep 2022 18:31:26 +0000
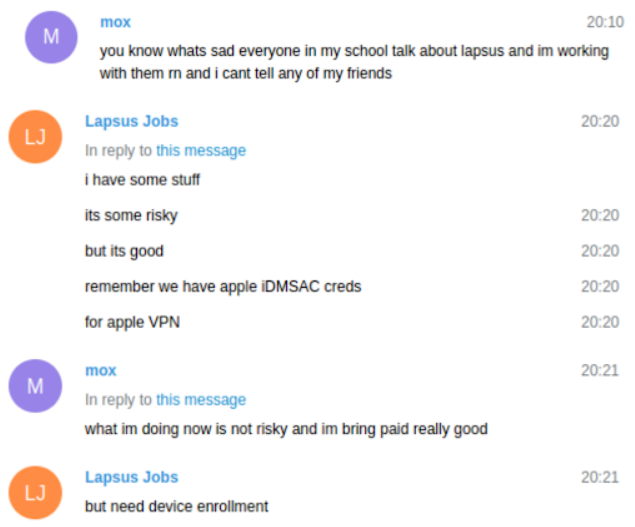
Events like this month’s breaches have happened before and will happen again. The task for defenders not directly affected by the Uber and Rockstar attacks, writes Chester Wisniewski, is to learn by putting your own team into those companies’ shoes.
Read More