U.S. Indicts 2 Top Russian Hackers, Sanctions Cryptex
Credit to Author: BrianKrebs| Date: Thu, 26 Sep 2024 14:54:07 +0000
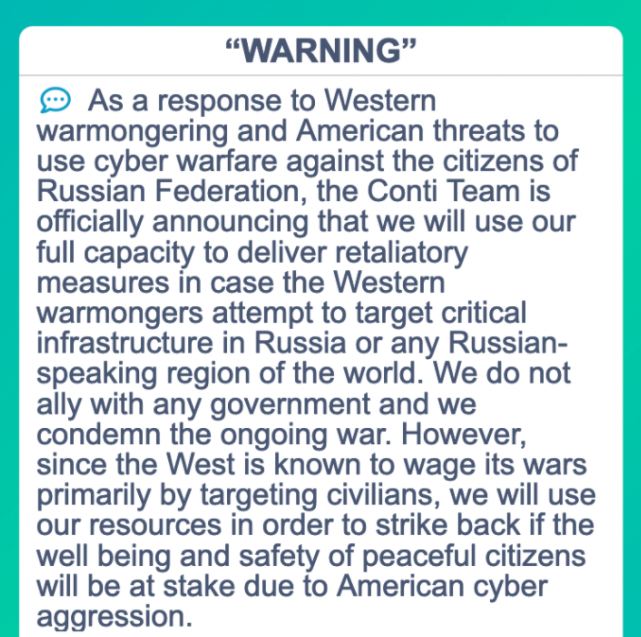
The United States today unveiled sanctions and indictments against the alleged proprietor of Joker’s Stash, a now-defunct cybercrime store that peddled tens of millions of payment cards stolen in some of the largest data breaches of the past decade. The government also indicted a top Russian cybercriminal known as Taleon, whose cryptocurrency exchange Cryptex has evolved into one of Russia’s most active money laundering networks.
Read More