Tech Firms Team Up to Take Down ‘WireX’ Android DDoS Botnet
Credit to Author: BrianKrebs| Date: Mon, 28 Aug 2017 14:06:08 +0000
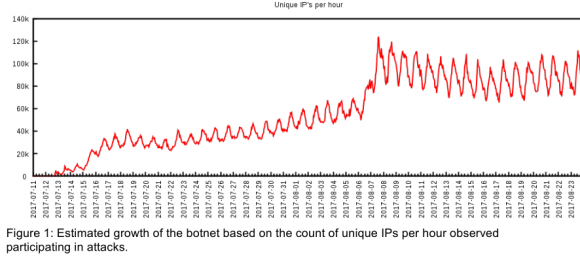
A half dozen technology and security companies — some of them competitors — issued the exact same press release today. This unusual level of cross-industry collaboration caps a successful effort to dismantle ‘WireX,’ an extraordinary new crime machine comprising tens of thousands of hacked Android mobile devices that was used this month to launch a series of massive cyber attacks. Experts involved in the takedown warn that WireX marks the emergence of a new class of attack tools that are more challenging to defend against and thus require broader industry cooperation to defeat.
Read more