The World’s Biggest Military Contractors Don’t Encrypt Their Websites
Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Mon, 09 Oct 2017 15:00:00 +0000
The websites of four of the five largest American defense and military contractors, which received a combined $95,278,712,971 last year from the US government, don’t use web encryption.
The main sites of Lockheed Martin, Boeing, Raytheon, and Northrop Grumman, all don’t have the standard web encryption HTTPS enabled by default, which leaves visitors of these sites exposed to common cyberattacks that could potentially allow hackers to infect them with malware. When tested on Friday, Generaldynamics.com was also not encrypted. On Monday, however, the site redirected to gd.com, which is served over HTTPS.
When websites have enabled HTTPS, the connection between the visitors and the site is encrypted, making it more private and secure. Without HTTPS, a hacker on your wireless network, internet service providers or governments, can track your every move online and also intercept and manipulate the data being exchanged between you and the site.
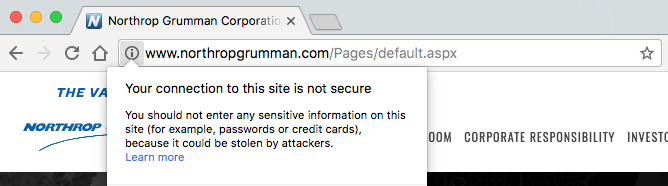
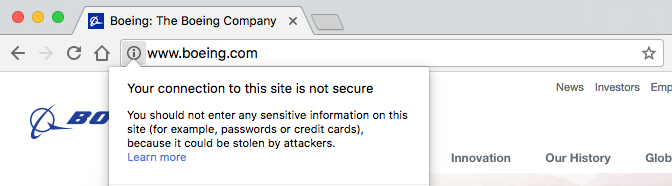
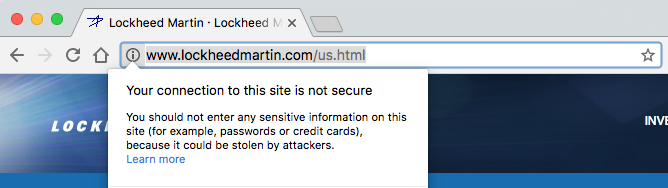
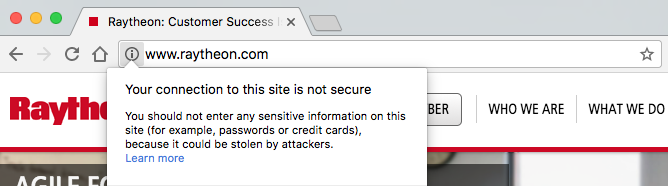
Lockheed Martin, Boeing, Raytheon, and Northrop Grumman did not respond to a request for comment.
For years, most of the web didn’t use web encryption. HTTPS used to slow down pages, getting a digital certificate to encrypt websites was costly and relatively complicated. And, in general, web developers believed HTTPS was only important on sensitive pages where users introduce passwords or credit card numbers.
But none of these arguments are valid today. Pages actually load faster with HTTPS, digital certificates are free, and security experts and web developers themselves understand that HTTPS—even on pages without sensitive, user-submitted content—is a good practice to protect visitors.
Read more: The Motherboard Guide To Not Getting Hacked
In fact, if a website doesn’t use HTTPS, hackers can hijack it with attacks known as Man-in-the-Middle or MiTM. In these kind of attacks, a hacker on the same Wi-Fi network or a government that has control over the country’s internet infrastructure can replace a legitimate, non-HTTPS website, or manipulate it to serve malware. Over the years, there have been countless, real-world, documented attacks where hackers impersonated non-HTTPS websites to infect victims with malware, or trick them into giving out their data. Even surveillance contractors, such as Hacking Team, took advantage of unencrypted sites, to hack users.
For all these reasons, the web is mostly encrypted now. As of this week, more than 60 percent of pages on the web are loaded over HTTPS, according to Firefox. This is the result of a concerted push by internet freedom and security activists, as well as companies such as Mozilla and Google, to promote the use of HTTPS across the whole internet.
“You are better protected from man in the middle attacks when visiting Pornhub than Raytheon or Lockheed.”
“For companies bidding on major cybersecurity contracts, lack of HTTPS-by-default in 2017 is a bad look,” John Scott-Railton, a senior researcher at the Citizen Lab, an academic group at the the University of Toronto’s Munk School of Global Affairs that studies internet security and digital rights, told Motherboard. “You are better protected from man in the middle attacks when visiting Pornhub than Raytheon or Lockheed.”
In fact, adult sites, such as Pornhub and YouPorn, as well as most major news and government websites, have switched to HTTPS by default in the last couple of years.
Google announced last year that it was planning to flag all non-HTTPS sites in Chrome with a “Not secure” warning in the next to the URL. Starting last January, sites that ask users for passwords or credit cards got flagged as insecure by Chrome. This month, the latest version of Chrome started giving sites where users enter any kind of data the same treatment in Incognito mode.
Soon, all sites—including those of multi-billion dollar companies— we’ll get the same treatment if they don’t make the switch.
“Eventually,” wrote Emily Schechter, from the Chrome security team, “we plan to show the ‘Not secure’ warning for all HTTP pages.”
Get six of our favorite Motherboard stories every day by signing up for our newsletter.