Cyber insurance: there’s bad news and there’s good news
Credit to Author: Doug Aamoth| Date: Mon, 16 May 2022 08:46:37 +0000
 Earlier this year, we asked 5,600 IT professionals about their experiences with cyber insurance.
Earlier this year, we asked 5,600 IT professionals about their experiences with cyber insurance.
The results are mixed, but the key takeaways are that cyber insurance is becoming harder and more expensive to get due in part to an increase in attacks. However, it’s meant that in order to get cyber insurance, companies are required to have solid protections in place, which means that overall defenses have improved.
Here’s a closer look at some of the data. You can download the full report here.
The bad news
 For starters, the overall threat environment is more challenging than ever. Over the last year, companies have been dealing with the following:
For starters, the overall threat environment is more challenging than ever. Over the last year, companies have been dealing with the following:
- A 57% increase in the volume of attack
- A 59% increase in the complexity of attacks
- A 53% increase in the impact of attacks
And when it comes to ransomware, things are getting worse. When asked if they’d been hit by ransomware in the last year, 66% of respondents said yes – up from 37% when we asked the same question last year.
What’s more, the average ransomware payment is now north of $800,000 whereas last year it was around $170,000.
Here’s what that means when it comes to trying to get cyber insurance in 2022. Our respondents reported the following:
- 54% said the level of cybersecurity they need to qualify is now higher
- 47% said policies are now more complex
- 40% said fewer companies offer cyber insurance
- 37% said the process takes longer
- 34% said it is more expensive
So: more frequent, more complex, more impactful attacks and fewer companies offering harder to get policies that are more expensive. Time for some good news, right?
The good news
 All the bad news listed above has become a forcing factor toward better security. The data indicates that 97% of those surveyed reported making changes to their defenses in order to secure insurance.
All the bad news listed above has become a forcing factor toward better security. The data indicates that 97% of those surveyed reported making changes to their defenses in order to secure insurance.
Of those who made changes…
- 64% have implemented new technologies and services
- 56% have increased staff training and education activities
- 52% have changed processes and behaviors
The other good news is that if you’re able to secure cyber insurance, it appears to be a worthwhile investment: 98% of respondents indicated that cyber insurance that included ransomware coverage paid out on related claims. Actual ransom payments were down as well, from 44% in 2019 to 40% in 2021.
More good news: we can help
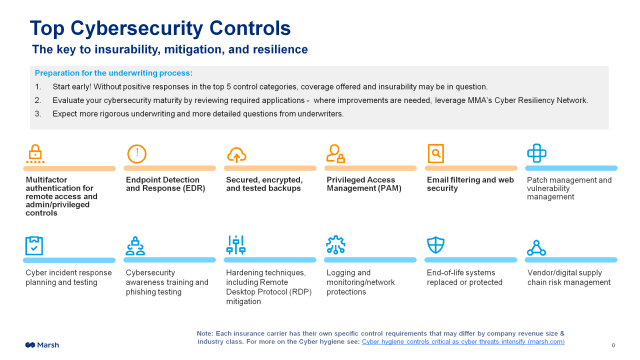
The first step toward getting cyber insurance: make sure you can get cyber insurance. According to leading cyber insurance broker Marsh McLennan Agency, the following security controls are must-haves…
- Multifactor authentication for remote access and privileged controls

- Endpoint detection and response (EDR)
- Secure, encrypted, and tested backups
- Privileged access management (PAM)
- Email filtering and web security
…while the following seven controls are desirable as well:
- Cyber incident response planning and testing
- Cybersecurity awareness training and phishing testing
- Hardening techniques, including Remote Desktop Protocol (RDP) mitigation
- Logging and monitoring/network protections
- End-of-life systems replaced or protected
- Vendor/digital supply chain risk management
Fortunately, the Sophos Managed Threat Response (MTR) service enables you to achieve many of these controls with single solution.
With Sophos MTR, you get our 24/7 threat hunting and response service, our powerful extended detection and response (XDR) tool, and Sophos’ world-class endpoint protection. Together they tick many of the cyber control boxes:
- Endpoint detection and response (EDR). Sophos MTR advanced gives you Sophos’ world-leading endpoint and workload protection to stop cyber attacks before they can run, together with 24/7 threat hunting, investigation, and response delivered by Sophos’ team of threat experts – to detect and stop human-led attacks. Should you wish to do the threat hunting yourself, you can do it with our XDR solution.
- Web security. Protects against malicious downloads and suspicious payloads delivered via browsers. Control features enable administrators to warn or block websites based on their category, block risky file types, and apply data leakage controls against web-based email and file sharing. Web Control for Cloud Workload environments secures data when users access virtual desktops that don’t sit behind a traditional web gateway.
- Privileged Access Management (PAM). Sophos XDR records all user activity, including authentication and Microsoft 365 audit logs to show changes to privilege settings. Also includes access to the Windows logs from the device and domain controller to see Windows events. It complements and enhances dedicated PAM solutions. Sophos Endpoint protection prevents attempts to harvest or steal user credentials directly from memory.
- Cyber incident response planning and testing. Sophos MTR provides 24/7 threat hunting, detection, and response delivered by an expert team as a fully-managed service. It includes unlimited incident response cover, so if you experience an event, our team of expert responders will step in and address it – at no extra cost.
- Hardening techniques, including remote desktop protocol mitigations. Sophos XDR enables you to identify when RDP has been used. Remote terminal allows administrators to enable and disable RDP policy. It also provides visibility into the RDP policy on all managed devices and detect changes to it.
- End of life systems replaced or protected. Sophos XDR identifies outdated and unsupported software and systems.
- Patch management and vulnerability management. Sophos XDR provides access to all applications on the device, version info, SHA256, patch info and their logs, including the application execution history, network connections, parent/child processes, and more. It also includes queries to check installed applications against online vulnerability information, and queries to identify security posture weaknesses in registry settings.
And that’s just with one service! We’ve also got network protection with Sophos Firewall, advanced filtering and business email compromise (BEC) protection with Sophos Email, phishing testing and training with Sophos Phish Threat, and several other products and services.
Visit Sophos.com to learn more and click here to read the report: Cyber Insurance 2022: Reality from the Infosec Frontline