Microsoft squares away 121-CVE Patch Tuesday for August
Credit to Author: Angela Gunn| Date: Wed, 10 Aug 2022 12:31:41 +0000
Microsoft on Tuesday released patches for 121 vulnerabilities in eight Microsoft product families. This includes 16 Critical-class issues affecting Azure, Exchange, and Windows. Once again the majority of CVEs affect Windows; the operating system takes the lion’s share of the CVEs with 61, followed by 44 for Azure. Three of the included Important-severity patches address boot-loader issues in non-Microsoft products and were apparently helmed not by Microsoft but by CERT/CC, as occasionally happens when one vulnerability affects multiple vendors. Two CVEs involving Windows Digital Media Receiver affect not only Windows but multiple digital formats.
One vulnerability, CVE-2022-30134, has been publicly disclosed. That elevation-of-privilege issue affects Exchange Server (versions 2013, 2016, and 2019), but would require the attacker to entice a victim to visit a specially crafted server share or website – a sufficiently high bar that Microsoft claims exploitation is unlikely.
Follina and Friends
One Important-class Remote Code Execution issue, affecting Microsoft Windows’ Remote Diagnostic Tool (MSDT), is currently under active exploit in the wild. The “DogWalk” issue, CVE-2022-34713, is closely related to the Follina issue (CVE-2022-30190) that burst onto the scene in late May. The previous CVE was quietly patched in June, and a defense-in-depth update was issued in July.
The MSDT issue covered in CVE-2022-34713 is actually older than the Follina variant; it was first reported to Microsoft in December 2019 by researcher Imre Rad. At that time, Microsoft’s investigation identified it to Rad as not being a security issue, at which point Rad disclosed his findings to the general public. Microsoft reassessed the bug and informed Rad on August 4 of this year that it is, in fact, a security issue. With interest and activity high around the matter, we recommend that administrators prioritize this CVE this month.
By the Numbers
- Total Microsoft CVEs: 121
- Total advisories shipping in update: 2
- Publicly disclosed: 1 (CVE-2022-30134)
- Exploitation detected: 1 (CVE-2022-34713)
- Exploitation more likely: 20 (both older and newer product versions)
- Severity
- Critical: 16
- Important: 103
- Moderate: 1
- Low: 1
- Impact
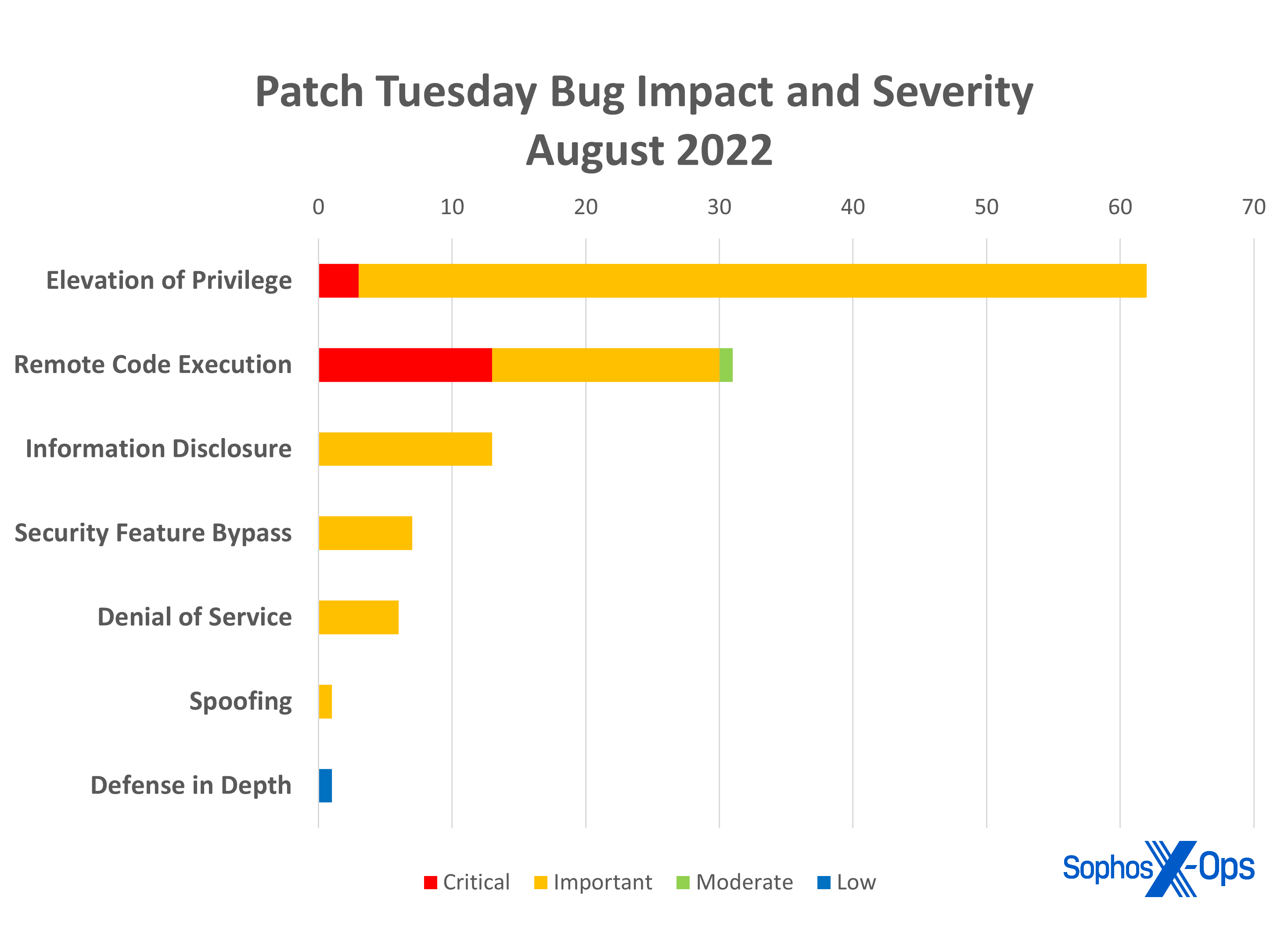
- Elevation of Privilege: 61
- Remote Code Execution: 31
- Information Disclosure: 13
- Security Feature Bypass: 8
- Denial of Service: 6
- Spoofing: 1
- Defense in Depth: 1
Figure 1: Approximately two-thirds of the Elevation of Privilege CVEs dominating the August patch collection belong to Azure
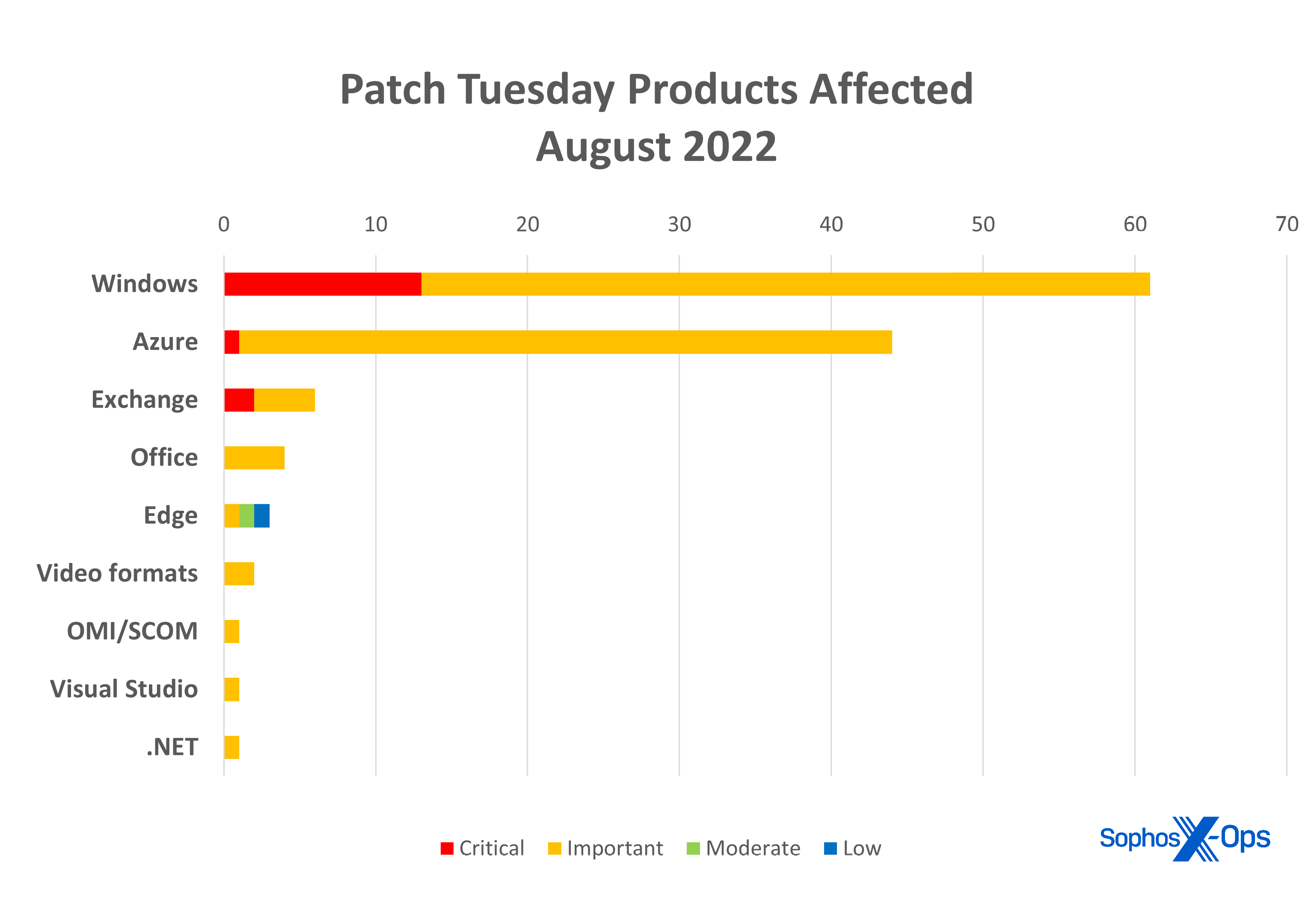
- Products
- Microsoft Windows: 61 (including two also classified as “video formats” below)
- Azure: 44
- Exchange: 6
- Microsoft Office: 4
- Edge: 3
- Video formats (AV1, HEIF, HEVC, VP9, WebP): 2 (also counted in Windows, above)
- .NET: 1
- System Center Operations Manager: Open Management Interface: 1
- Visual Studio: 1
Figure 2: The two CVEs affecting multiple digital file formats (CVE-2022-35746, CVE-2022-35749) are represented twice in this chart (under both ‘Windows’ and “Video formats”), since anyone using those formats outside Windows is presumably affected
Notable Vulnerabilities
Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability (CVE-2022-34713)
As noted above, this CVE involves a close variant of the CVE-2022-30190 issue flagged in late May as the heart of “Follina.” The most likely attack vector for this path-traversal flaw would be a specially crafted file, either sent to the user via email (and opened by the user) or hosted on an external site to which the user was routed. The issue affects all versions of Windows.
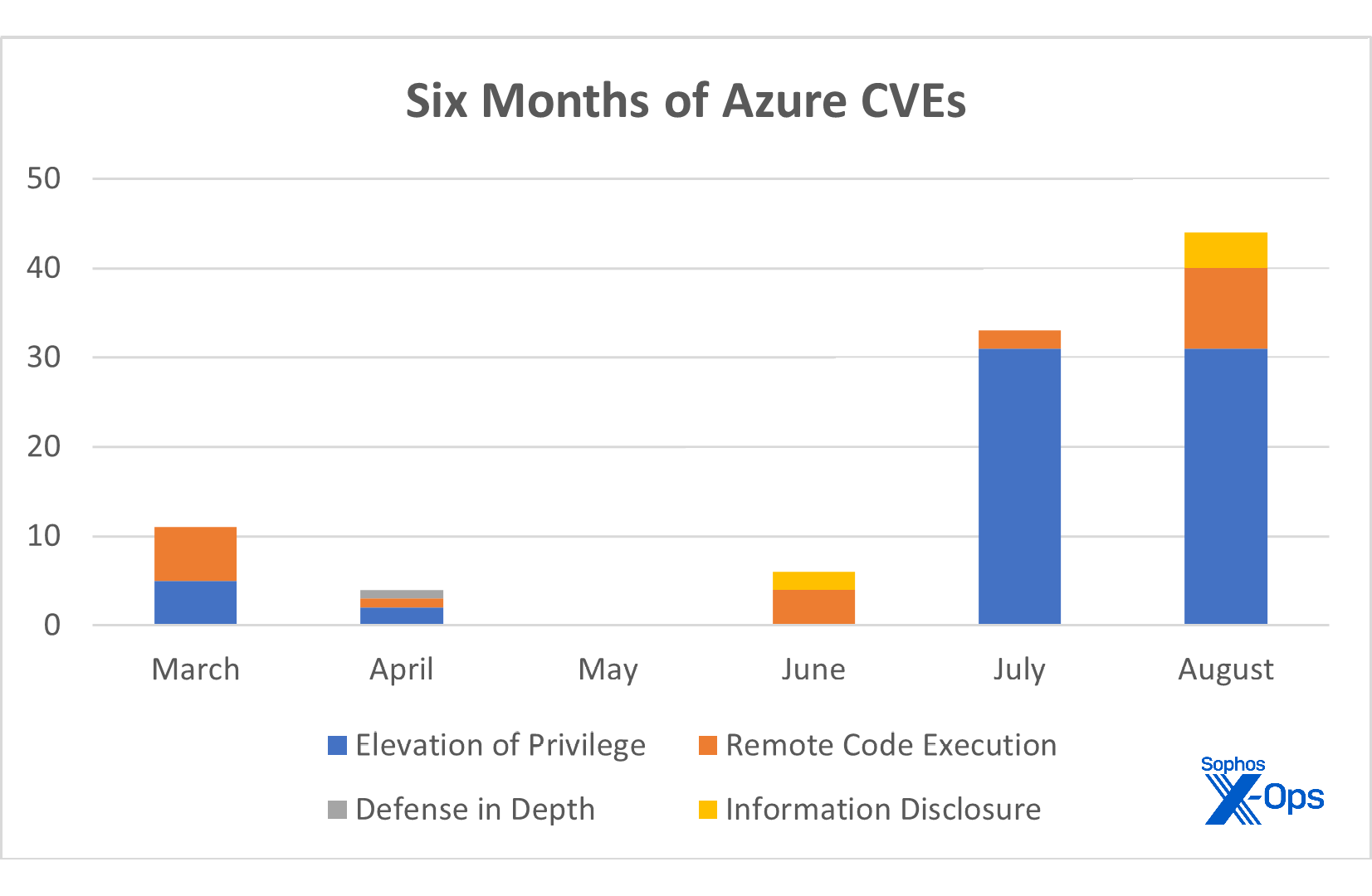
44 CVEs, Azure
We’ve noticed a trend in the last few months: Azure patches. Lots of them. The volume of patched vulnerabilities in Azure has rocketed over the summer, as shown in Figure 3:
Figure 3: It’s not your imagination: It has indeed been a cruel summer for Azure administrators
A variety of finders are credited for the patched issues, some working with known and respected research houses and others more obscure. The vulns themselves are harder to easily differentiate, at least by title; for example, in the past six months we’ve seen six “Azure RTOS GUIX Studio Remote Code Execution Vulnerability,” 29 “Azure Site Recovery Elevation of Privilege Vulnerability,” and 31 “Azure Site Recovery Elevation of Privilege Vulnerability” CVEs.
CERT/CC: CVE-2022-34301 Eurosoft Boot Loader Bypass (CVE-2022-34301)
CVE-2022-34302 – CERT/CC: CVE-2022-34302 New Horizon Data Systems Inc Boot Loader Bypass (CVE-2022-34302)
CERT/CC: CVE-20220-34303 Crypto Pro Boot Loader Bypass (CVE-2022-34303)
This trio of security-feature bypass CVEs arrives with CNA (CVE Numbering Authority) numbers not from Microsoft, as is usual for Microsoft patches, but from the US CERT Coordination Center. GRUB is another boot loader (GNU GRand Unified Bootloader), and one of the two Advisories this month (“Microsoft Guidance for Addressing Security Feature Bypass in GRUB”, ADV200011) touches on that.
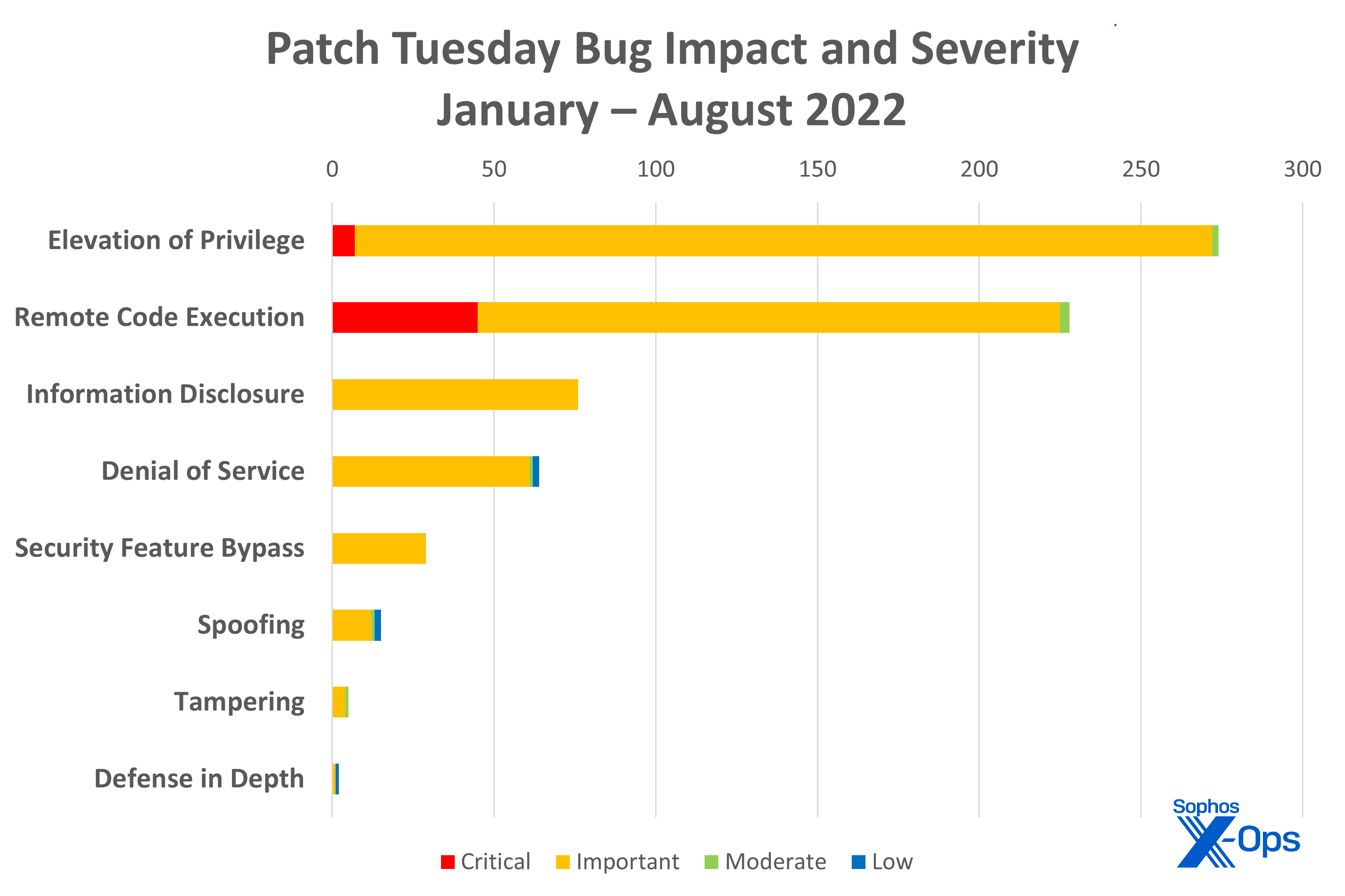
Figure 4: Elevation-of-privilege issues continue to dominate in 2022, though odds are that any given RCE issue this year is of greater severity
Sophos protection
(Ever wondered about behavior names, by the way? Sophos’ naming conventions line up with the MITRE ATT&CK framework. Details are available elsewhere on our site.)
Part of our current protections against the CVE-2022-34713 bug involve a blocking detection. Sophos will continue to evaluate the most effective ways to address the malicious CAB files associated with CVE-2022-34713.
As you can every month, if you don’t want to wait for your system to pull down the updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your particular system’s architecture and build number.