Brazil Arrests ‘USDoD,’ Hacker in FBI Infragard Breach
Credit to Author: BrianKrebs| Date: Fri, 18 Oct 2024 12:33:51 +0000
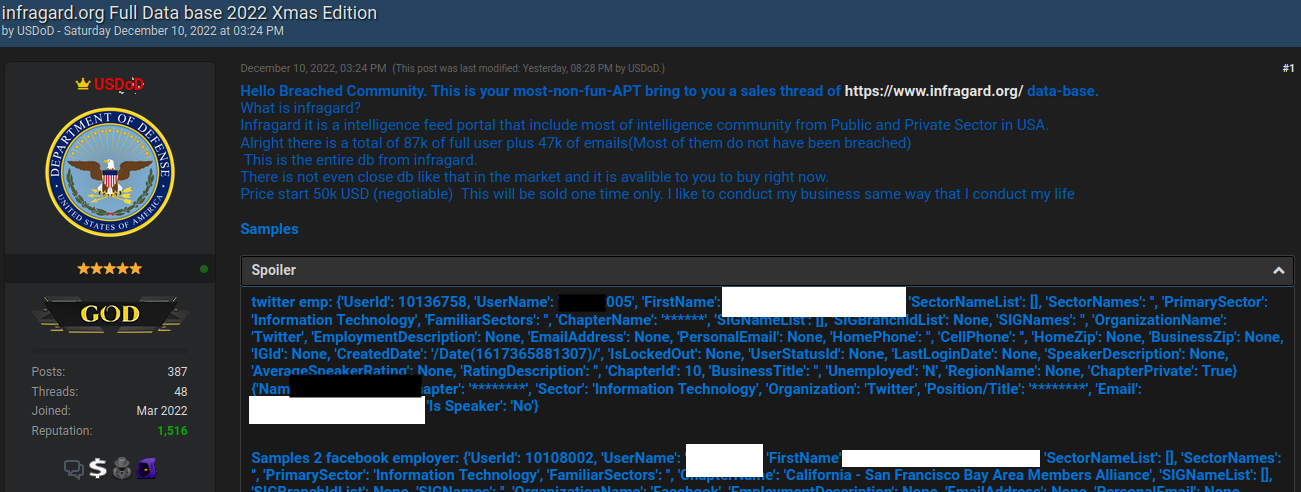
Brazilian authorities reportedly have arrested a 33-year-old man on suspicion of being “USDoD,” a prolific cybercriminal who rose to infamy in 2022 after infiltrating the FBI’s InfraGard program and leaking contact information for 80,000 members. More recently, USDoD was behind a breach at the consumer data broker National Public Data that led to the leak of Social Security numbers and other personal information for a significant portion of the U.S. population.
Read More