Clever malvertising attack uses Punycode to look like KeePass’s official website
Threat actors are known for impersonating popular brands in order to trick users. In a recent malvertising campaign, we observed a malicious…
Read moreThreat actors are known for impersonating popular brands in order to trick users. In a recent malvertising campaign, we observed a malicious…
Read moreCategories: Threat Intelligence Tags: malvertising Tags: keepass Tags: punycode Tags: malware Tags: ads Tags: google Threat actors are doubling down on brand impersonation by using lookalike domain names. |
The post Clever malvertising attack uses Punycode to look like KeePass’s official website appeared first on Malwarebytes Labs.
Read moreCredit to Author: Jovi Umawing| Date: Mon, 10 Dec 2018 15:00:56 +0000
 | |
| Phishing is more problematic on smartphones than on desktops. Not only that, approaches to handling phishing attacks on mobile are quite different because their techniques are also different. So, how can users sniff out a mobile phish? Let us count the ways. Categories: Tags: ad-networking phishinghomograph attacksHTTPSiOSMobilephishingphishing appsPunycodesmishingSocial Phishingunicodeurl paddingvishing |
The post Something else is phishy: How to detect phishing attempts on mobile appeared first on Malwarebytes Labs.
Read more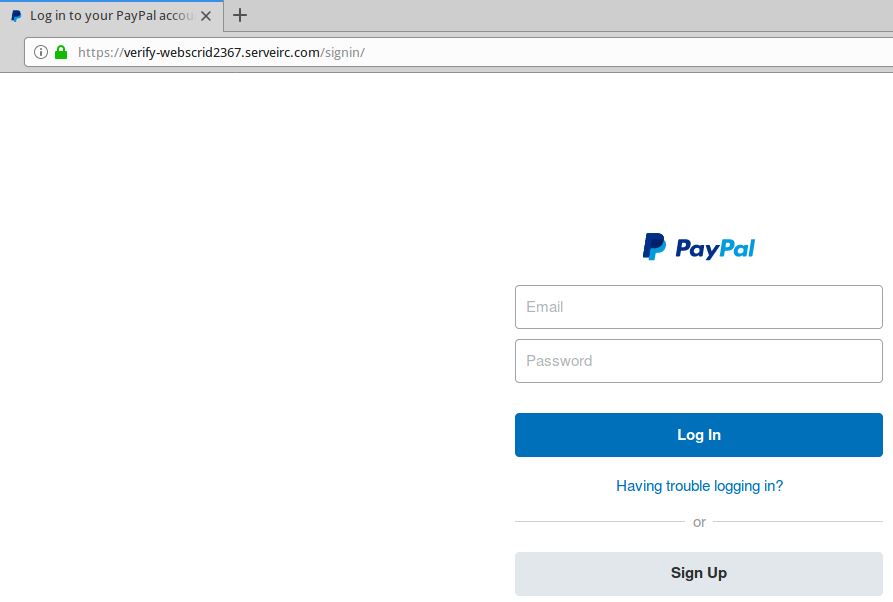
Credit to Author: BrianKrebs| Date: Mon, 26 Nov 2018 14:57:53 +0000
Maybe you were once advised to “look for the padlock” as a means of telling legitimate e-commerce sites from phishing or malware traps. Unfortunately, this has never been more useless advice. New research indicates that half of all phishing scams are now hosted on Web sites whose Internet address includes the padlock and begins with “https://”.
Read more
Credit to Author: Jason Zhang| Date: Mon, 30 Jul 2018 15:08:01 +0000
Spammers increasingly use PDF’s ability to embed hyperlinks into documents to direct recipients of malicious PDFs to open malicious Web sites. We’ve discovered a spam campaign using internationalized URLs embedded in PDF document attachments.<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/m7P5mGmCiUk” height=”1″ width=”1″ alt=””/>
Read more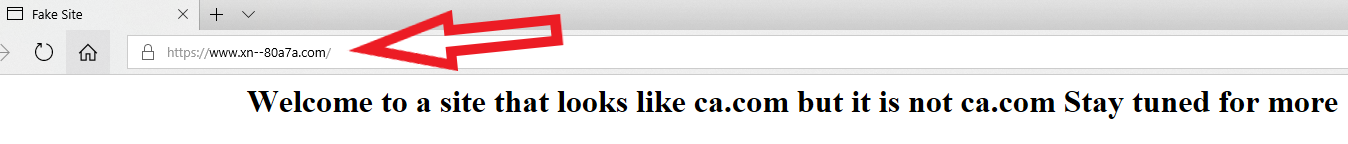
Credit to Author: BrianKrebs| Date: Thu, 08 Mar 2018 16:55:13 +0000
How good are you at telling the difference between domain names you know and trust and imposter or look-alike domains? The answer may depend on how familiar you are with the nuances of internationalized domain names (IDNs), as well as which browser or Web application you’re using. For example, how does your browser interpret the following domain? I’ll give you a hint: Despite appearances, it is most certainly not the actual domain for software firm CA Technologies (formerly Computer Associates Intl Inc.), which owns the original ca.com domain name: https://www.са.com/ Go ahead and click on the link above or cut-and-paste it into a browser address bar. If you’re using Google Chrome, Apple’s Safari, or some recent version of Microsoft’s Internet Explorer or Edge browsers, you should notice that the address converts to “xn--80a7a.com.” This is called “punycode,” and it allows browsers to render domains with non-Latin alphabets like Cyrillic and Ukrainian. Below is what it looks like in Edge on Windows 10; Google Chrome renders it much the same way. Notice what’s in the address bar (ignore the “fake site” and “Welcome to…” text, which was added as a courtesy by the person who registered this domain):
Read moreCredit to Author: Jérôme Segura| Date: Mon, 04 Dec 2017 22:48:49 +0000
 | |
| The most prolific gate to the RIG exploit kit is coming in a different flavor. The Seamless campaign is now using a domain name with foreign characters translated by Punycode. Categories: Tags: phishingPunycoderamnitRamnit TrojanRIGRIGEKSeamlesstrojan |
The post Seamless campaign serves RIG EK via Punycode (updated) appeared first on Malwarebytes Labs.
Read moreCredit to Author: Jérôme Segura| Date: Mon, 04 Dec 2017 22:48:49 +0000
 | |
| The most prolific gate to the RIG exploit kit is coming in a different flavor. The Seamless campaign is now using a domain name with foreign characters translated by Punycode. Categories: Tags: phishingPunycoderamnitRamnit TrojanRIGRIGEKSeamlesstrojan |
The post Seamless campaign serves RIG EK via Punycode appeared first on Malwarebytes Labs.
Read more