Context-sensitive defenses in Sophos Endpoint

Credit to Author: Tom Walsh| Date: Tue, 26 Sep 2023 14:03:57 +0000
Sophos continues to deliver innovative new protection to guard customers from attack.
Read MoreRSS Reader for Computer Security Articles

Credit to Author: Tom Walsh| Date: Tue, 26 Sep 2023 14:03:57 +0000
Sophos continues to deliver innovative new protection to guard customers from attack.
Read More
Credit to Author: Sergei Shevchenko| Date: Tue, 17 Mar 2020 08:00:58 +0000
Security software frequently blocks “bundleware” installers – software distribution tools that bundle their advertised applications with (usually undesired) additional software – as potentially undesirable applications. But one widely-used software distribution tool for MacOS applications goes to great lengths to avoid being blocked as “bundleware” – using a number of anti-forensics techniques that are more common […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/n8Txqmat4RA” height=”1″ width=”1″ alt=””/>
Read MoreCredit to Author: Editor| Date: Tue, 25 Feb 2020 13:36:43 +0000
A new APT-style attack combines a bypassing technique with a multi-platform payload to target both Windows and Linux cloud workloads. Stop the attack with technical advice from Sophos.<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/q61MwUx5OsI” height=”1″ width=”1″ alt=””/>
Read More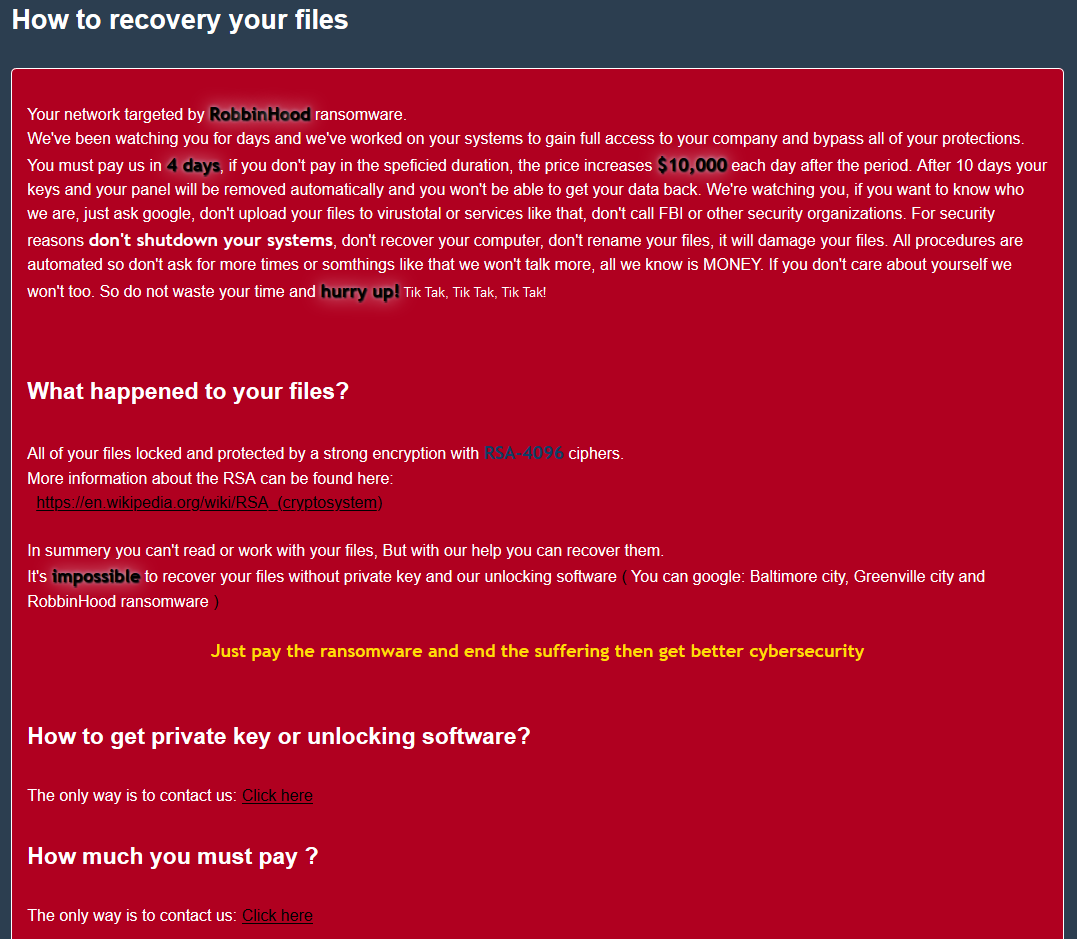
Credit to Author: Andrew Brandt| Date: Thu, 06 Feb 2020 15:22:24 +0000
Sophos has been investigating two different ransomware attacks where the adversaries deployed a legitimate, digitally signed hardware driver in order to delete security products from the targeted computers just prior to performing the destructive file encryption portion of the attack. The signed driver, part of a now-deprecated software package published by Taiwan-based motherboard manufacturer Gigabyte, […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/uepwaOU8_Ek” height=”1″ width=”1″ alt=””/>
Read More
Credit to Author: Jörg Schindler| Date: Wed, 18 Dec 2019 11:01:15 +0000
Die Bedrohungslandschaft hat sich im abgelaufenen Jahr mehrfach stark verändert. Anlass genug also, immer wieder neu in die Zukunft zu blicken, um das Verständnis dieser Trends zu schärfen und um sich als Unternehmen in der Cybersicherheit gut aufzustellen. Fünf Experten von Sophos haben einen genauen Blick auf die wichtigsten Security-Faktoren geworfen, die sich 2020 maßgeblich […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/9IQwSaFgKHY” height=”1″ width=”1″ alt=””/>
Read More
Credit to Author: Andrew Brandt| Date: Thu, 23 Jan 2020 00:22:26 +0000
The SophosLabs Offensive Security team answers your questions about the CVE-2020-0601 (aka Chain of Fools and Curveball) vulnerability.<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/682tR8CBAA8″ height=”1″ width=”1″ alt=””/>
Read More
Credit to Author: J.J. Thompson| Date: Wed, 15 Jan 2020 13:01:37 +0000
As geopolitical interest increases, discussions of threat intelligence increase which increases pressure on security operations teams to provide answers to customers and to senior leadership.<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/pQqkg_WT2eU” height=”1″ width=”1″ alt=””/>
Read More
Credit to Author: Mat Gangwer| Date: Wed, 15 Jan 2020 10:02:05 +0000
In addition to normal tradecraft adaptations, any time a change in the geopolitical landscape takes place, cyberattack campaigns and adversary behaviors typically shift as well. The recent events with Iran and the United States offer a relevant use case for organizations and have highlighted the benefit of having a threat intelligence driven hunting process. The […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/SIgRbmduM5E” height=”1″ width=”1″ alt=””/>
Read More