“Inhospitality” malspam campaign targets hotel industry
Credit to Author: Andrew Brandt| Date: Tue, 19 Dec 2023 11:00:33 +0000
Sophos X-Ops is warning the hospitality industry that a campaign targeting hotels worldwide with password-stealing malware is using emailed complaints about service problems or requests for information as a social engineering lure to gain the trust of the campaign’s targets, before sending them links to malicious payloads.
The attackers are using a methodology similar to the one Sophos X-Ops uncovered in the months leading up to the US federal tax filing deadline in April 2023: They initially contact the target over email that contains nothing but text, but with subject matter a service-oriented business (like a hotel) would want to respond to quickly. Only after the target responds to the threat actor’s initial email does the threat actor send a followup message linking to what they claim is details about their request or complaint.
The social engineering angle spans a wide variety of subject matter, but can be categorized into two generalized buckets: complaints about serious issues the sender claims to have experienced in a recent stay, or requests for information to help with a potential future booking.
Sophos X-Ops has already briefed representatives of the Retail and Hospitality Information Sharing and Analysis Center (RH-ISAC) about this attack targeting their industry during the busy end-of-year holiday travel season.
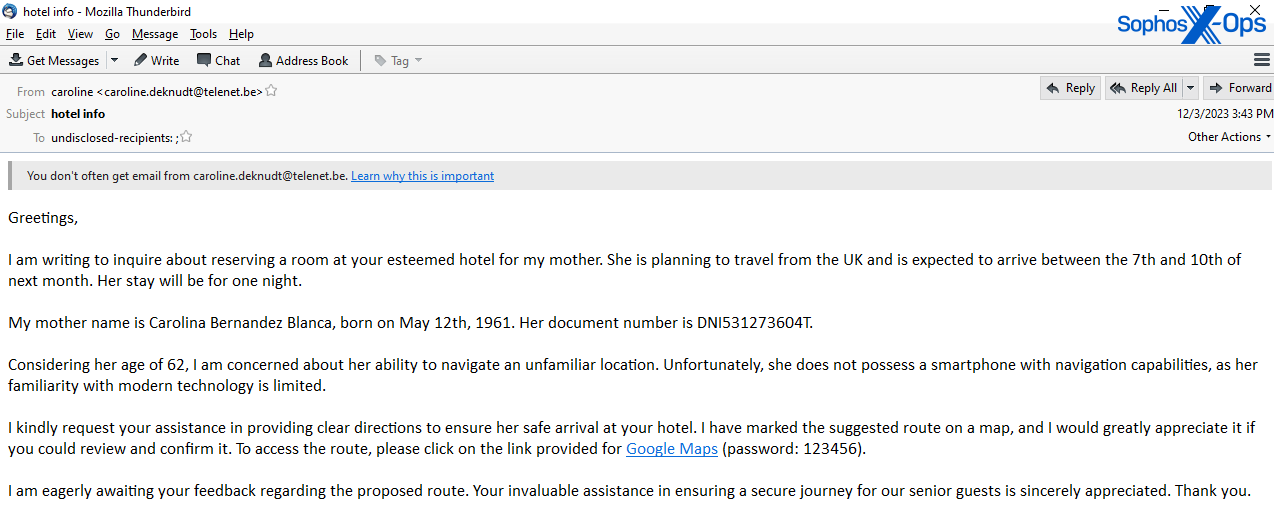
I am writing to inquire
The content of the ‘complaint’-style messages range from allegations of violent attacks or bigoted behavior by members of the hotel staff, to assertions that the “guest” had items stolen or lost from their room. The ‘requests for information’-type messages included emails asking for accommodations for someone with severe allergies, messages about how the hotel could support a business meeting, or inquiries about accessibility within the hotel for a disabled or elderly guest.
In every case, once a representative from the hotel responded to the initial inquiry asking for more information, the threat actor replied with a message that – the attacker claims – links to documentation or evidence supporting their claims or requests. The “documentation” is not actual documentation, but the malware payload, wrapped in a password-protected archive file.
The links point to public cloud storage services, such as Google Drive, and the body of the message contains a password (usually numeric) that the recipient is prompted to use to open the Zip or Rar archive at the other end of the download link.
Common characteristics of email messages in the campaign
The messages attackers send to hotel staff share some traits that make them more suspicious and merit additional caution by recipients.
Like many successful malspam campaigns, the messages are engineered to play on emotions and on the target’s desire to render assistance – a self-selecting trait for successful people working in the hospitality industry.
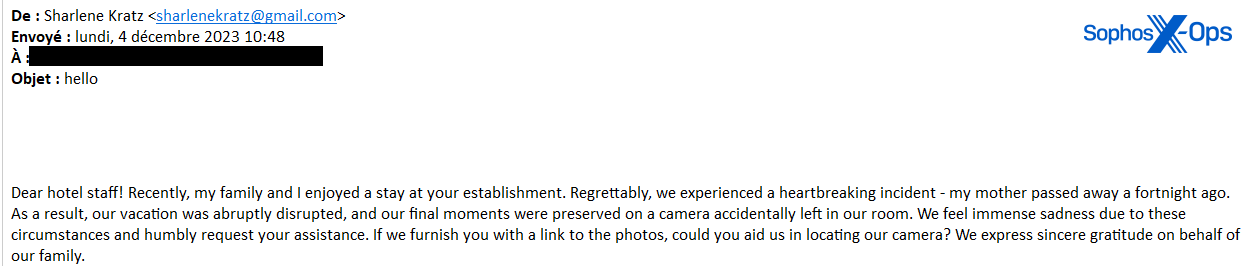
In one example, the threat actor tells a hotel staffer that they left a camera behind in a room that contains photos of a recently deceased relative, and asks the hotel for help locating the camera.
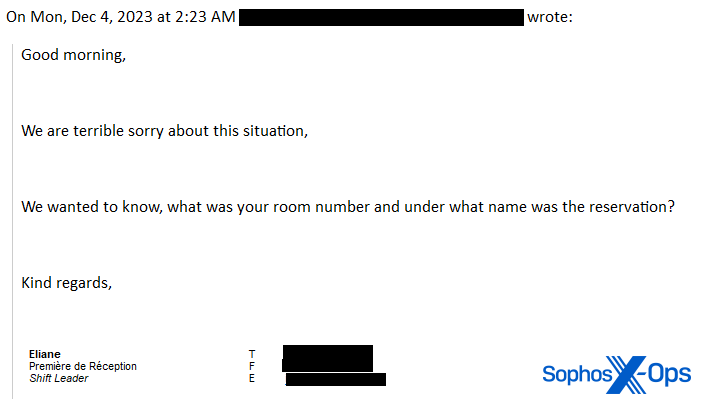
When the hotel staff replied, asking for the room number and name the reservation was under, the threat actor replies, feigning exasperation.
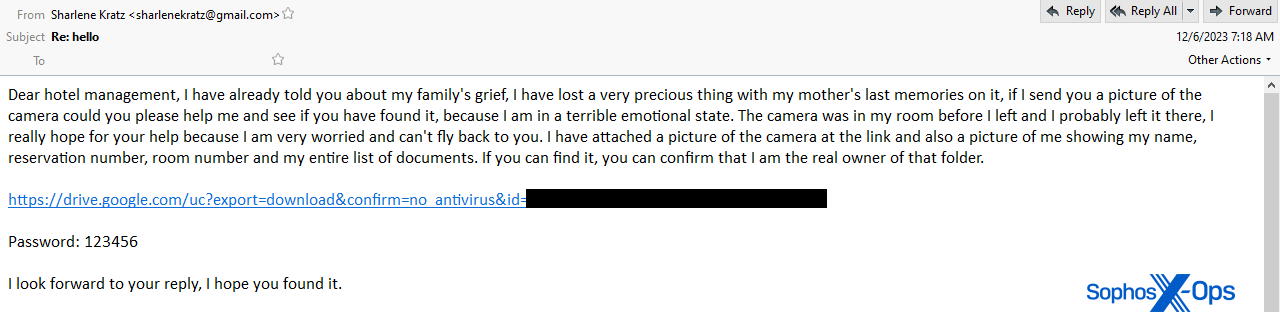
“I have already told you about my family’s grief, I have lost a very precious thing with my mother’s last memories on it, if I send you a picture of the camera could you please help me” along with a link to a file hosted on Google Drive, and the text “Password: 123456” below the link.
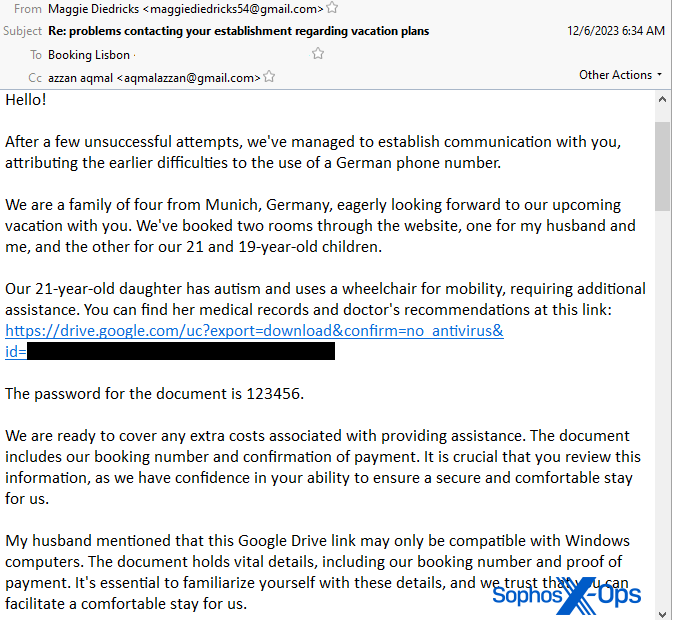
In another example, the threat actor emails a hotel and asks them to reply because they “have been unable to contact you through the website or by phone.” When the booking agent from the hotel asks them to provide more details about their plans, the threat actor replies, claiming they have booked rooms through the website but need to make arrangements for the accommodation of a family member with a disability. Their second email links to a zip file hosted on Google Drive they claim contains “medical records and doctor’s recommendations” and, again, a password of 123456 needed to open the file.
In that message, the threat actor adds the following “My husband mentioned that this Google Drive link may only be compatible with Windows computers. The document holds vital details, including our booking number and proof of payment. It’s essential to familiarize yourself with these details.”
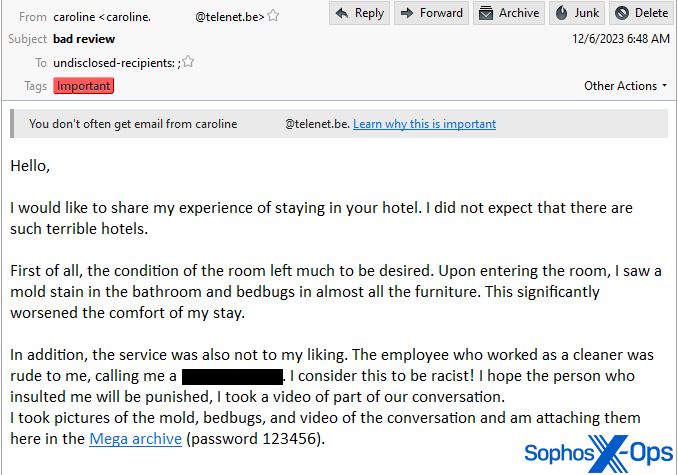
In what might be the most egregious example, the threat actor asked for contact with a manager to address a problem they had at the hotel. Once the manager replies, the threat actor writes “I did not expect there are such terrible hotels,” describing a horrifying (fictitious) experience that included mouldy walls, “bedbugs in almost all the furniture” that “significantly worsened the comfort of my stay,” and an employee who used a racist epithet. The email links to a RAR archive file hosted on the Mega.nz cloud hosting provider, also with a password of 123456, that the sender alleges contains a video of the confrontation between the guest and staff member.
The emails all contrive an excuse to share documentation with the hotel workers via cloud storage, from Google Drive, Mega.nz, Dropbox, or from an address in the content hosting space of the chat platform Discord. The malicious payloads linked from these messages were compressed in either the Zip or Rar compression format, and used one of the following list of passwords.
- 1111
- 123456
- 2023
- info2023
- hotel
- 501949
We saw many more examples of creative writing by the threat actor. Emails complained about guests contracting a variety of diseases; concerns over allergic reactions to cleaning products; allegations of being poisoned in the hotel; stains on mattresses, walls, or in bathrooms; insects on furniture in the rooms; purses, rings, expensive watches or cameras being left behind or stolen from rooms; a need for accommodations or assistance for guests with limited mobility or access to technology; and rude, violent, or bigoted behavior by staff directed at the guest.
Payloads designed to evade sandboxing
The malware payloads themselves were created with the intent to make it more difficult to scan or detect the malicious content.
The archives are all password-protected, which prevents the cloud service hosting them from casually scanning the contents and detecting whether the payload is malicious.
When unpacked from their archive containers, the malware itself has characteristics that also help it elude immediate detection.
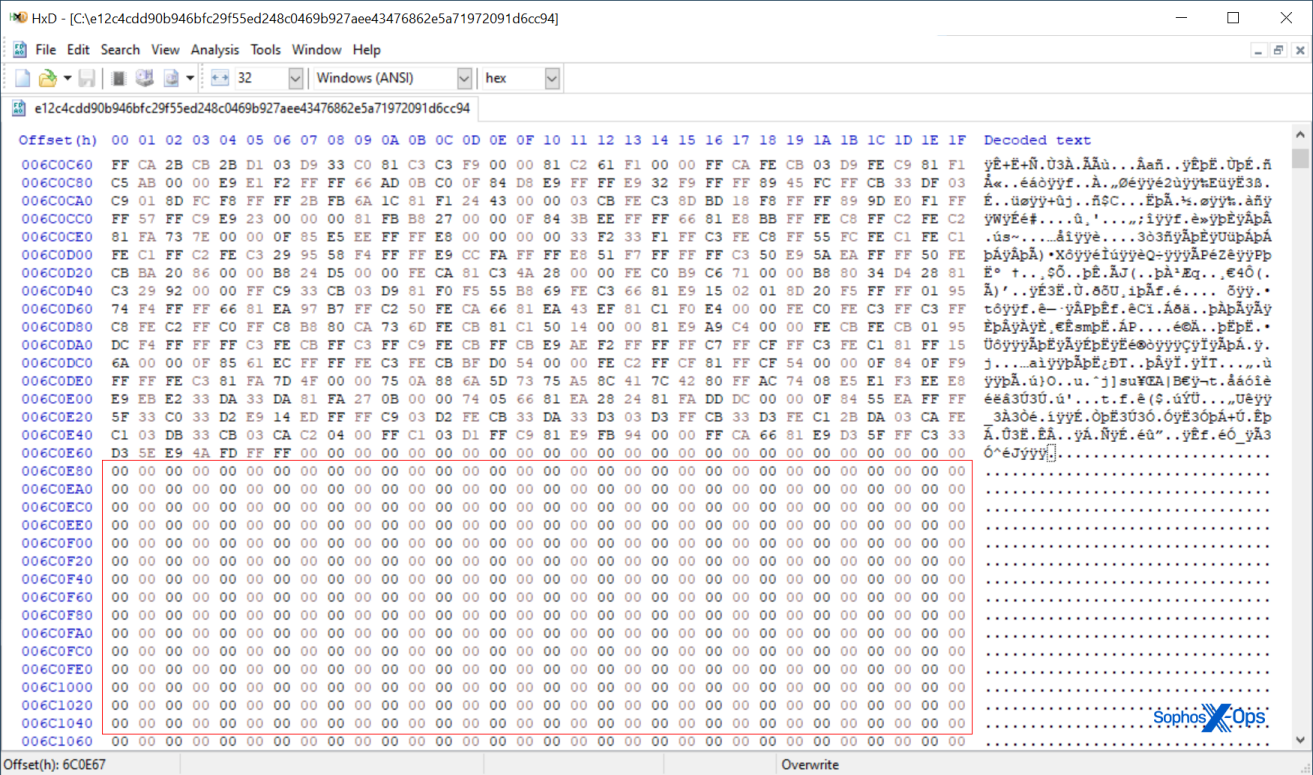
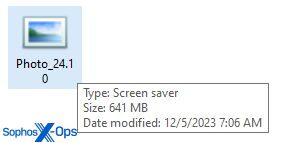
Many of the unzipped or de-archived payload files are vastly larger than a typical executable. Several of the samples we uncovered weigh in at well above 600MB in size. Files of this size might be missed by static endpoint protection scanners designed to process much smaller files.
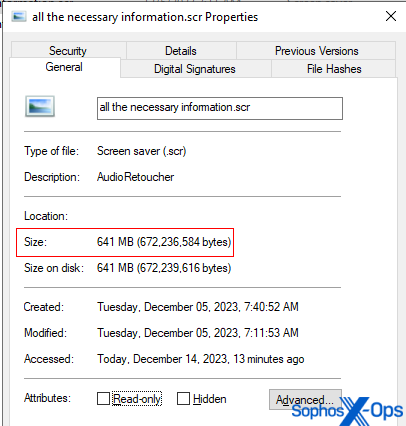 The vast majority of the internal content of those files was just bytes containing zeroes, used as space-filler.
The vast majority of the internal content of those files was just bytes containing zeroes, used as space-filler.
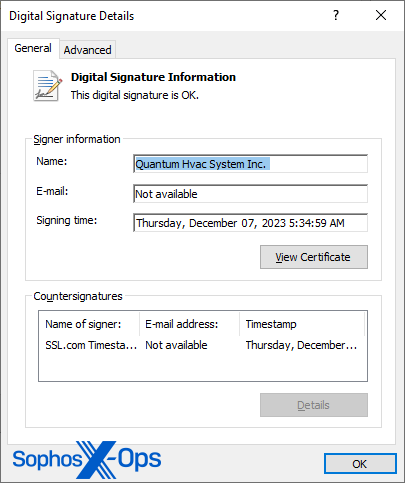
Nearly all of the samples have been signed with a code-validation certificate. Many of the certificates are brand new – obtained during the course of the campaign’s operational period – and queries of some of those certificates indicate the signature remains valid for many of the samples, while others appear to be faked or counterfeit, and do not pass validation.
Some endpoint protection tools will automatically exclude executables with valid signatures from scanning; Some will only look for the presence of a certificate, not bothering to check whether it is valid.
Simple but effective password-stealer malware
Most of the samples appear to be variants of a malware family variously called Redline Stealer or Vidar Stealer. Despite their size, 99% of the volume of the malware executables (with either an .exe or .scr extension) that are greater than 600MB in size are just zeroes. The malware code is tacked on to the end of the very large files with jump commands that leap over the empty space.
When executed, the malware immediately connects to a URL on the Telegram encrypted messaging service. The URL points to a chat room, the title of which is a web address used for the bot’s command-and-control. At the time we tested this malware, the C2 address was an IP address and a high-numbered, nonstandard TCP port.
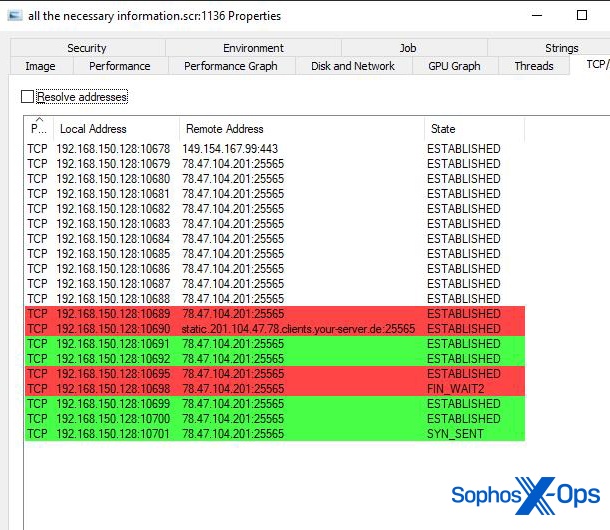 The bot then connects to the address it retrieves from the Telegram channel and downloads a payload capable of a variety of features from that address. It uses HTTP POST requests to the C2 server to submit telemetry about the infected machine, including details of account information saved in the browser and screenshots of the desktop. The server delivers information the bot can use to encrypt its communication in response.
The bot then connects to the address it retrieves from the Telegram channel and downloads a payload capable of a variety of features from that address. It uses HTTP POST requests to the C2 server to submit telemetry about the infected machine, including details of account information saved in the browser and screenshots of the desktop. The server delivers information the bot can use to encrypt its communication in response.
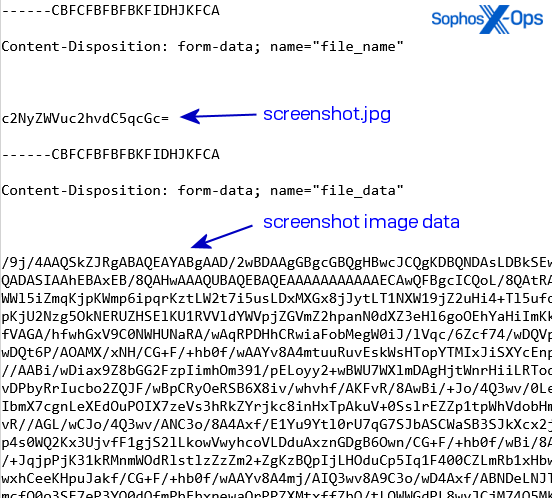 The malware does not establish persistence on the host machine. It runs once, does its work extracting then exfiltrating the data it wants to steal, then quits. In addition to passwords and cookie information, the bot profiles the machine it is running on, and sends everything about it to the bot controller. The samples we ran did not even delete themselves after running.
The malware does not establish persistence on the host machine. It runs once, does its work extracting then exfiltrating the data it wants to steal, then quits. In addition to passwords and cookie information, the bot profiles the machine it is running on, and sends everything about it to the bot controller. The samples we ran did not even delete themselves after running.
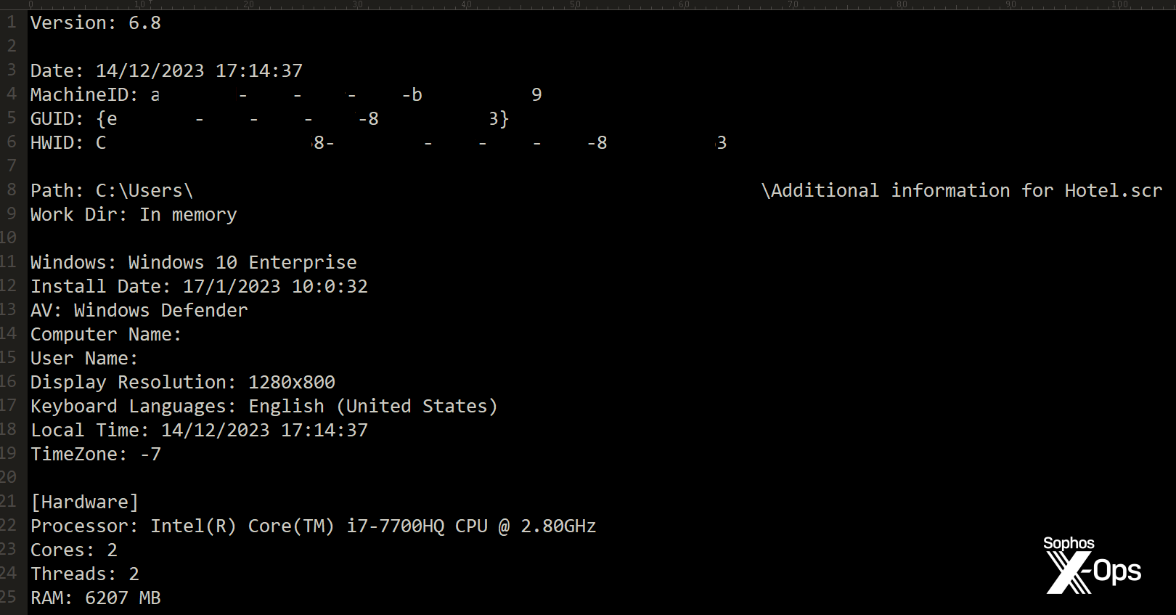 At the time of this writing, Sophos X-Ops has retrieved more than 50 unique samples from cloud storage where the files were hosted by the threat actors conducting this campaign. We have also reported the malicious links to the various cloud storage providers hosting the malware. Most of those samples displayed few-to-no detections in Virustotal.
At the time of this writing, Sophos X-Ops has retrieved more than 50 unique samples from cloud storage where the files were hosted by the threat actors conducting this campaign. We have also reported the malicious links to the various cloud storage providers hosting the malware. Most of those samples displayed few-to-no detections in Virustotal.
Sophos has published indicators of compromise to our Github repository.
Sophos endpoint security products will detect the malware as Troj/Agent-BKJE. Attempts to exfiltrate credentials are blocked using the behavioral detection Creds_2D.
Acknowledgments
Sophos X-Ops thanks Senior Threat Researchers Felix Weyne and Anand Ajjan for spotting the campaign in its early stages and raising the alarm, and staff at the RH-ISAC for their help disseminating warnings about this attack to their members and the hotel industry at large.