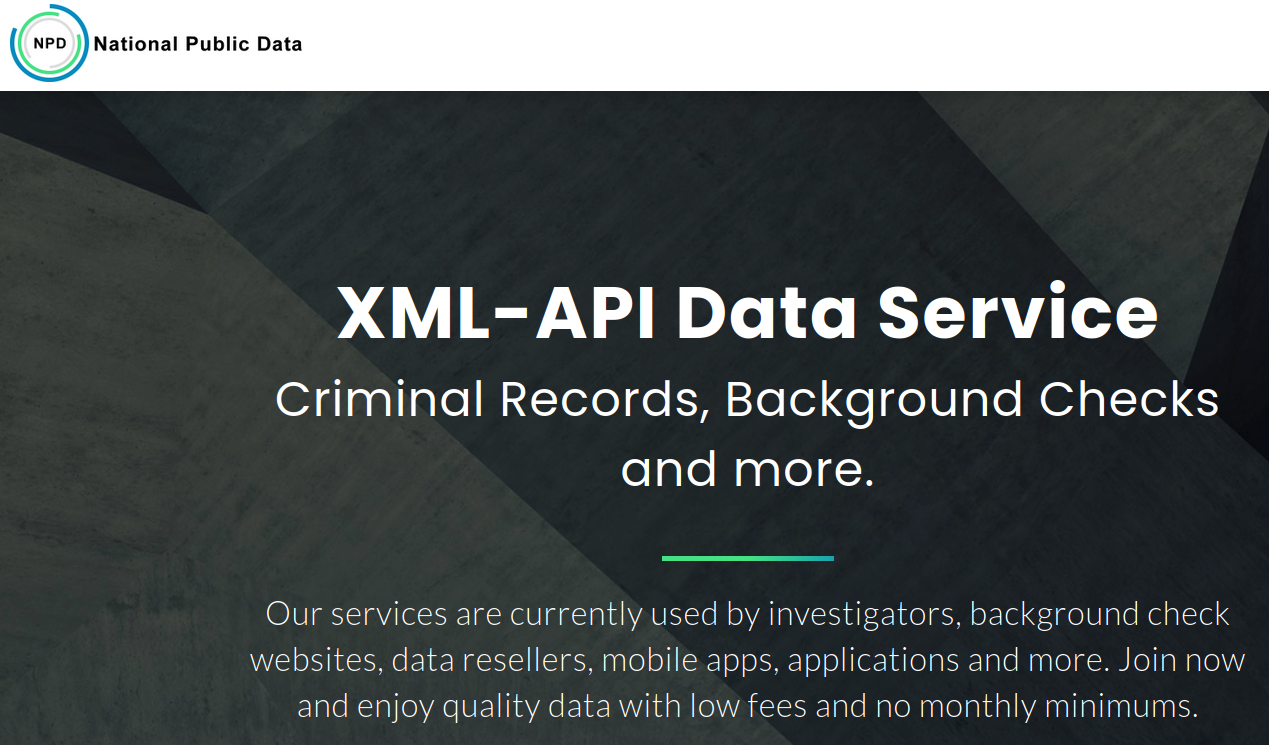
The Slow-Burn Nightmare of the National Public Data Breach

Credit to Author: Lily Hay Newman| Date: Fri, 16 Aug 2024 18:31:13 +0000
Social Security numbers, physical addresses, and more—all available online. After months of confusion, leaked information from a background check firm underscores the long-term risks of data breaches.
Read More