Apple slaps hard against ‘mercenary’ surveillance-as-a-service industry
Credit to Author: Jonny Evans| Date: Thu, 07 Jul 2022 06:17:00 -0700
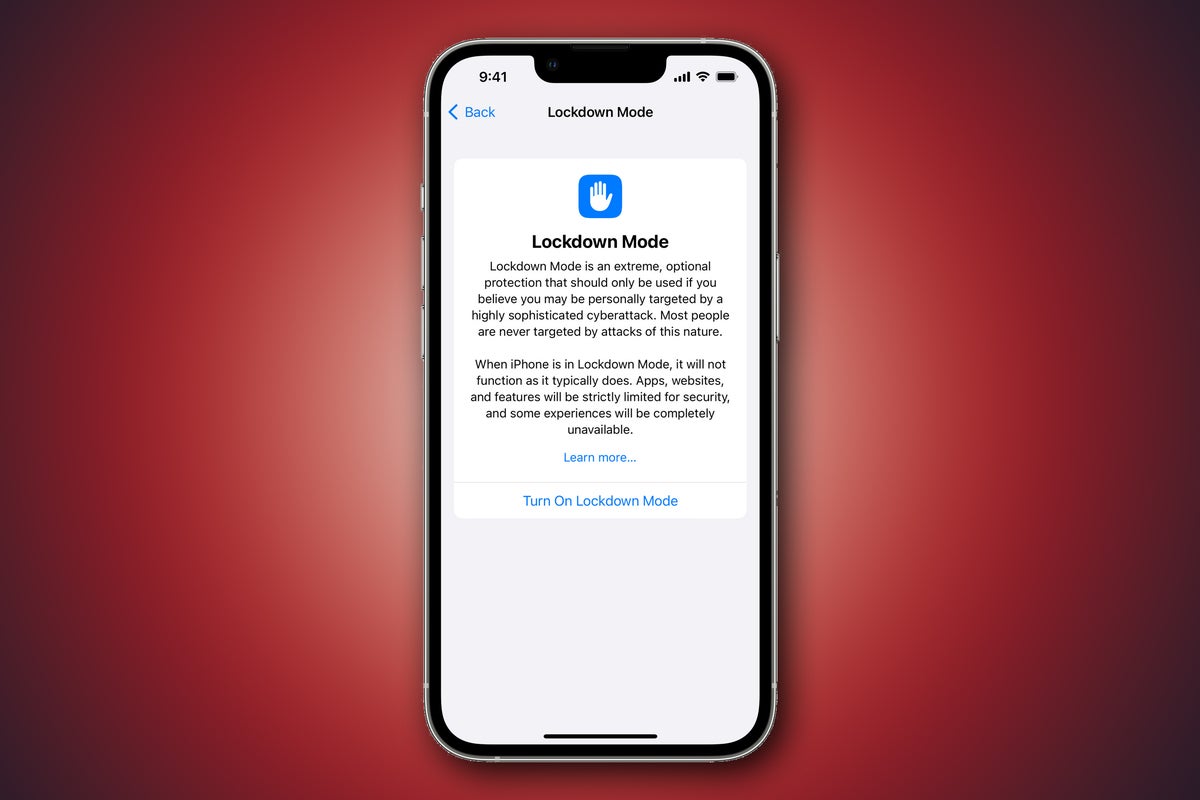
Apple has struck a big blow against the mercenary “surveillance-as-a-service” industry, introducing a new, highly secure Lockdown Mode to protect individuals at the greatest risk of targeted attacks. The company is also offering millions of dollars to support research to expose such threats.
Starting in iOS 16, iPadOS 16 and macOS Ventura, and available now in the latest developer-only betas, Lockdown Mode hardens security defenses and limits the functionalities sometimes abused by state-sponsored surveillance hackers. Apple describes this protection as “sharply reducing the attack surface that potentially could be exploited by highly targeted mercenary spyware.”