Data: E-Retail Hacks More Lucrative Than Ever
Credit to Author: BrianKrebs| Date: Tue, 30 Apr 2019 20:13:03 +0000
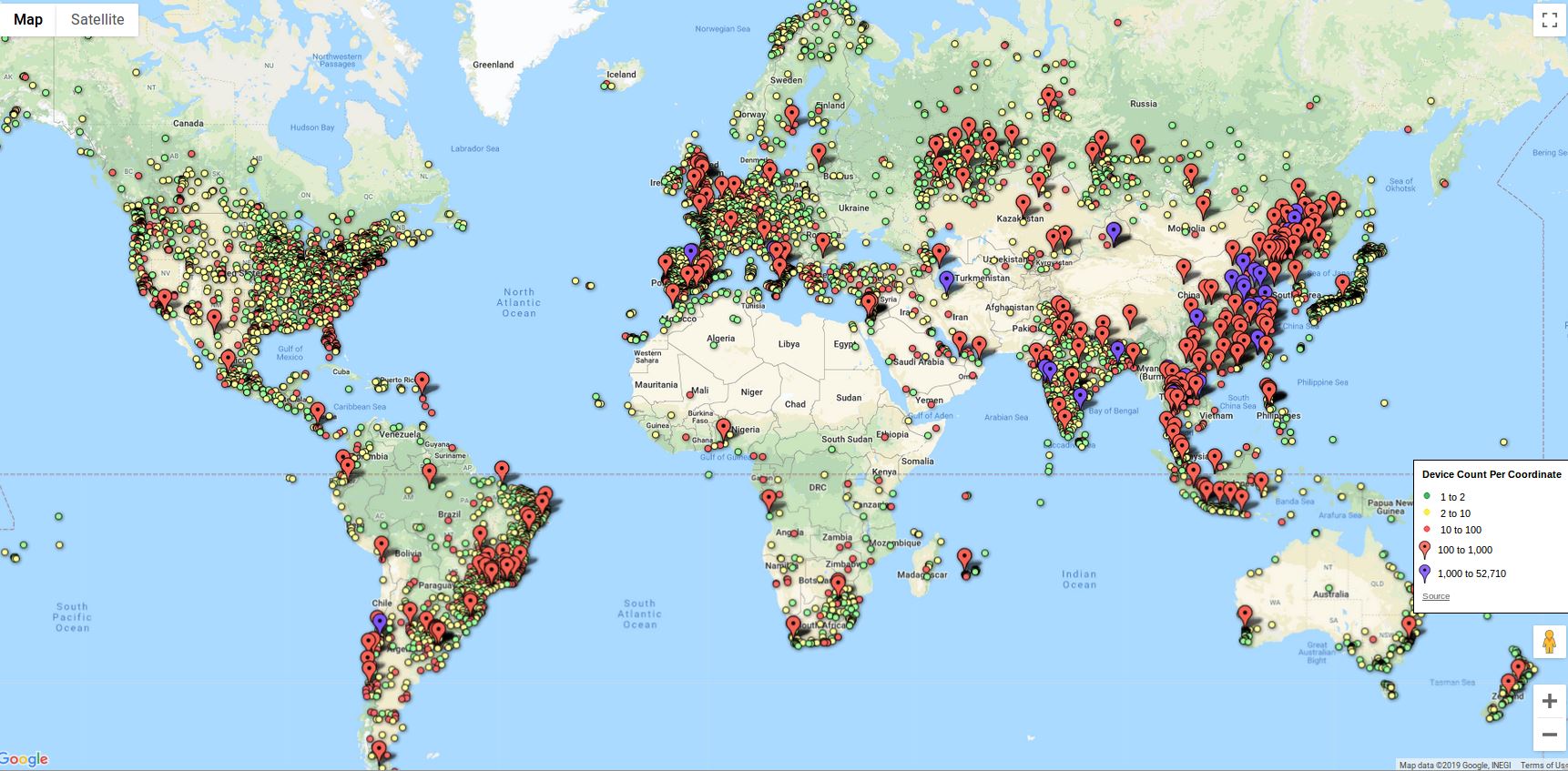
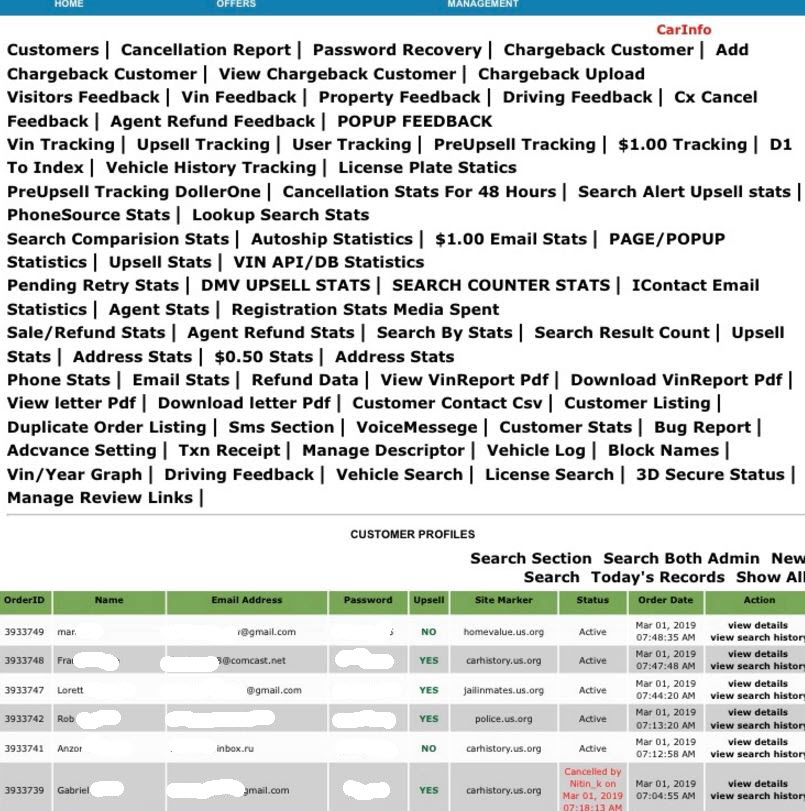
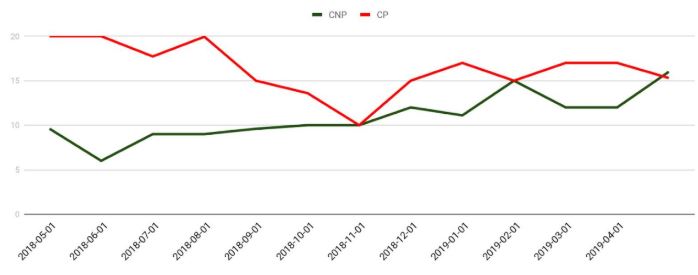
For many years and until quite recently, credit card data stolen from online merchants has been worth far less in the cybercrime underground than cards pilfered from hacked brick-and-mortar stores. But new data suggests that over the past year, the economics of supply-and-demand have helped to double the average price fetched by card-not-present data, meaning cybercrooks now have far more incentive than ever to target e-commerce stores.
Read More