Reddit Breach Highlights Limits of SMS-Based Authentication
Credit to Author: BrianKrebs| Date: Thu, 02 Aug 2018 00:55:17 +0000
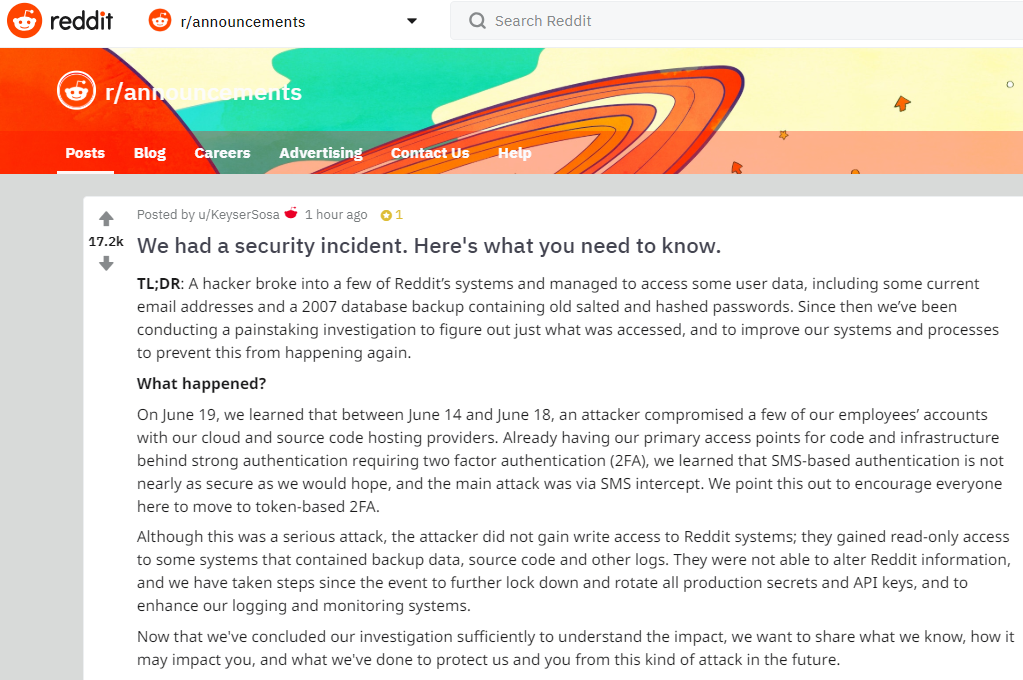
Reddit.com today disclosed that a data breach exposed some internal data, as well as email addresses and passwords for some Reddit users. As Web site breaches go, this one doesn’t seem too severe. What’s interesting about the incident is that it showcases once again why relying on mobile text messages (SMS) for two-factor authentication (2FA) can lull companies and end users into a false sense of security.
In a post to Reddit, the social news aggregation platform said it learned on June 19 that between June 14 and 18 an attacker compromised a several employee accounts at its cloud and source code hosting providers.
Reddit said the exposed data included internal source code as well as email addresses and obfuscated passwords for all Reddit users who registered accounts on the site prior to May 2007. The incident also exposed the email addresses of some users who had signed up to receive daily email digests of specific discussion threads.
Of particular note is that although the Reddit employee accounts tied to the breach were protected by SMS-based two-factor authentication, the intruder(s) managed to intercept that second factor.
“Already having our primary access points for code and infrastructure behind strong authentication requiring two factor authentication (2FA), we learned that SMS-based authentication is not nearly as secure as we would hope, and the main attack was via SMS intercept,” Reddit disclosed. “We point this out to encourage everyone here to move to token-based 2FA.”
Reddit didn’t specify how the SMS code was stolen, although it did say the intruders did not hack Reddit employees’ phones directly. Nevertheless, there are a variety of well established ways that attackers can intercept one-time codes sent via text message.
In one common scenario, known as a SIM-swap, the attacker masquerading as the target tricks the target’s mobile provider into tying the customer’s service to a new SIM card that the bad guys control. A SIM card is the tiny, removable chip in a mobile device that allows it to connect to the provider’s network. Customers can request a SIM swap when their existing SIM card has been damaged, or when they are switching to a different phone that requires a SIM card of another size.
Another typical scheme involves mobile number port-out scams, wherein the attacker impersonates a customer and requests that the customer’s mobile number be transferred to another mobile network provider. In both port-out and SIM swap schemes, the victim’s phone service gets shut off and any one-time codes delivered by SMS (or automated phone call) get sent to a device that the attackers control.
APP-BASED AUTHENTICATION
A more secure alternative to SMS involves the use of a mobile app — such as Google Authenticator or Authy — to generate the one-time code that needs to be entered in addition to a password. This method is also sometimes referred to as a “time-based one-time password,” or TOTP. It’s more secure than SMS simply because the attacker in that case would need to steal your mobile device or somehow infect it with malware in order to gain access to that one-time code. More importantly, app-based two-factor removes your mobile provider from the login process entirely.
Fundamentally, two-factor authentication involves combining something you know (the password) with either something you have (a device) or something you are (a biometric component, for example). The core idea behind 2FA is that even if thieves manage to phish or steal your password, they still cannot log in to your account unless they also hack or possess that second factor.
Technically, 2FA via mobile apps and other TOTP-based methods are more accurately described as “two-step authentication” because the second factor is supplied via the same method as the first factor. For example, even though the second factor may be generated by a mobile-based app, that one-time code needs to be entered into the same login page on a Web site along with user’s password — meaning both the password and the one-time code can still be subverted by phishing, man-in-the-middle and credential replay attacks.
SECURITY KEYS
Probably the most secure form of 2FA available involves the use of hardware-based security keys. These inexpensive USB-based devices allow users to complete the login process simply by inserting the device and pressing a button. After a key is enrolled for 2FA at a particular site that supports keys, the user no longer needs to enter their password (unless they try to log in from a new device). The key works without the need for any special software drivers, and the user never has access to the code — so they can’t give it or otherwise leak it to an attacker.
The one limiting factor with security keys is that relatively few Web sites currently allow users to use them. Some of the most popular sites that do accept security keys include Dropbox, Facebook and Github, as well as Google’s various services.
Last week, KrebsOnSecurity reported that Google now requires all of its 85,000+ employees to use security keys for 2FA, and that it has had no confirmed reports of employee account takeovers since the company began requiring them at the beginning of 2017.
The most popular maker of security keys — Yubico — sells the basic model for $20, with more expensive versions that are made to work with mobile devices. The keys are available directly from Yubico, or via Amazon.com. Yubico also includes a running list of sites that currently support keys for authentication.
If you’re interested in migrating to security keys for authentication, it’s a good idea to purchase at least two of these devices. Virtually all sites that I have seen which allow authentication via security keys allow users to enroll multiple keys for authentication, in case one of the keys is lost or misplaced.
I would encourage all readers to pay a visit to twofactorauth.org, and to take full advantage of the most secure 2FA option available for any site you frequent. Unfortunately many sites do not support any kind of 2-factor authentication — let alone methods that go beyond SMS or a one-time code that gets read to you via an automated phone call. In addition, some sites that do support more robust, app- or key-based two-factor authentication still allow customers to receive SMS-based codes as a fallback method.
If the only 2FA options offered by a site you frequent are SMS and/or phone calls, this is still better than simply relying on a password. But it’s high time that popular Web sites of all stripes start giving their users more robust authentication options like TOTP and security keys. Many companies can be nudged in that direction if enough users start demanding it, so consider using any presence and influence you may have on social media platforms to make your voice heard on this important issue.