How else to detect hidden cameras and microphones | Kaspersky official blog
Credit to Author: Enoch Root| Date: Mon, 11 Jul 2022 16:17:30 +0000
In 2019, when a survey was carried out among travelers who make use of short-term rentals, 11% of participants said they’d found surveillance cameras in their rented accommodation. Moreover, about two-thirds of those surveyed worry that unscrupulous apartment owners may use hidden cameras.
Just recently, we wrote about how Apple AirTags can be used to stalk people and steal cars. The problem of covert filming in rental accommodation is similar in nature — the deployment of seemingly useful devices for nefarious purposes.
The issue of covert surveillance isn’t likely to go away soon; rather — just the opposite. First, a simple wireless video camera that transmits real-time data over Wi-Fi can be purchased for peanuts. Second, modern technology has advanced to the level where even cheap spy devices have become quite miniature and easy to hide amid an interior.
There are several ways to find hidden cameras; the easiest of which is to scan a room in the dark with a phone camera to identify video cameras with an infrared light source (go here to read about this and other detection methods). However, the effectiveness of these methods leaves much to be desired, and the demand for more reliable ways to detect spy devices increases as they proliferate.
Therefore, attempts are constantly being made to create more hi-tech anti-spy technologies. The most advanced system was recently proposed by researchers at Carnegie Mellon University in the U.S. They found a way that potentially allows anyone to detect hidden IoT devices in a rented room using a smartphone app.
App-based spy detection
The authors of the paper decided to implement the following scenario. The “test guests” are given the keys to a rented apartment. After checking in, they open the special Lumos app on their smartphone and wait for about half an hour.
Then they walk around the perimeter of each room holding the phone, which determines the coordinates of detected transmitters. After that, the app not only shows a list of detected “smart” devices, but also indicates their location. IoT devices are displayed in augmented reality (AR): information about the location of smart devices is superimposed on the image from the phone’s camera. The researchers made a demo video of the app:
Looks neat, but how does it work? The researchers assume that a typical landlord who rents out an apartment through Airbnb or a similar service will not spend time installing really sophisticated spy devices — this is both costly and, in most cases, redundant. Instead, they’re more likely to buy something cheap and simple from the local store.
It’s not hard to make a rough list of devices that could potentially be a privacy threat. The most obvious of them is a video camera that transmits image and sound over Wi-Fi. It might also be a smart speaker configured to constantly eavesdrop on conversations, a smart TV, or even a specialized security system — but home-grade, like Amazon Ring.
Because all Wi-Fi-connected devices operate in a common frequency band they must coordinate data transmission with each other. Based on such open information, Lumos can find nearby wireless devices, identify their type (telling a webcam from a smart light bulb, for example), and even give an approximate location with an accuracy of 1.5 meters.

The spy device detection system adds an AR visual aid to the smartphone’s camera image to indicate the presence of a wireless camera nearby. Source
Lumos in detail
Some of you are probably already thinking: “Enough chit-chat, where can I download the thing?!” Unfortunately, you can’t for now. What’s more, in the prototypes it proved impossible to implement all the functionality using smartphones alone. That’s because Lumos has slightly higher requirements than typical smartphone Wi-Fi capabilities: it’s not enough for the system to simply connect to an access point and communicate only through that. Instead, Lumos has to scan all data packets transmitted over the air from all devices nearby. But the ability to sniff the airwaves is blocked in all smartphones.
Theoretically, it can be done on a rooted Android device (that is, one on which the owner has superuser rights that give full access to the system), but the researchers went in a different direction. They built two test systems, the first consisting of a smartphone with a Raspberry Pi microcomputer connected to it, and the second being a laptop with a special camera.
In the first case, the Raspberry Pi listened to the Wi-Fi transmission; in the second, the laptop did (such functionality is easier to implement on a full-fledged computer than on a smartphone). Accordingly, either the smartphone camera or the AR camera connected to the laptop was used for visual detection of hidden devices.
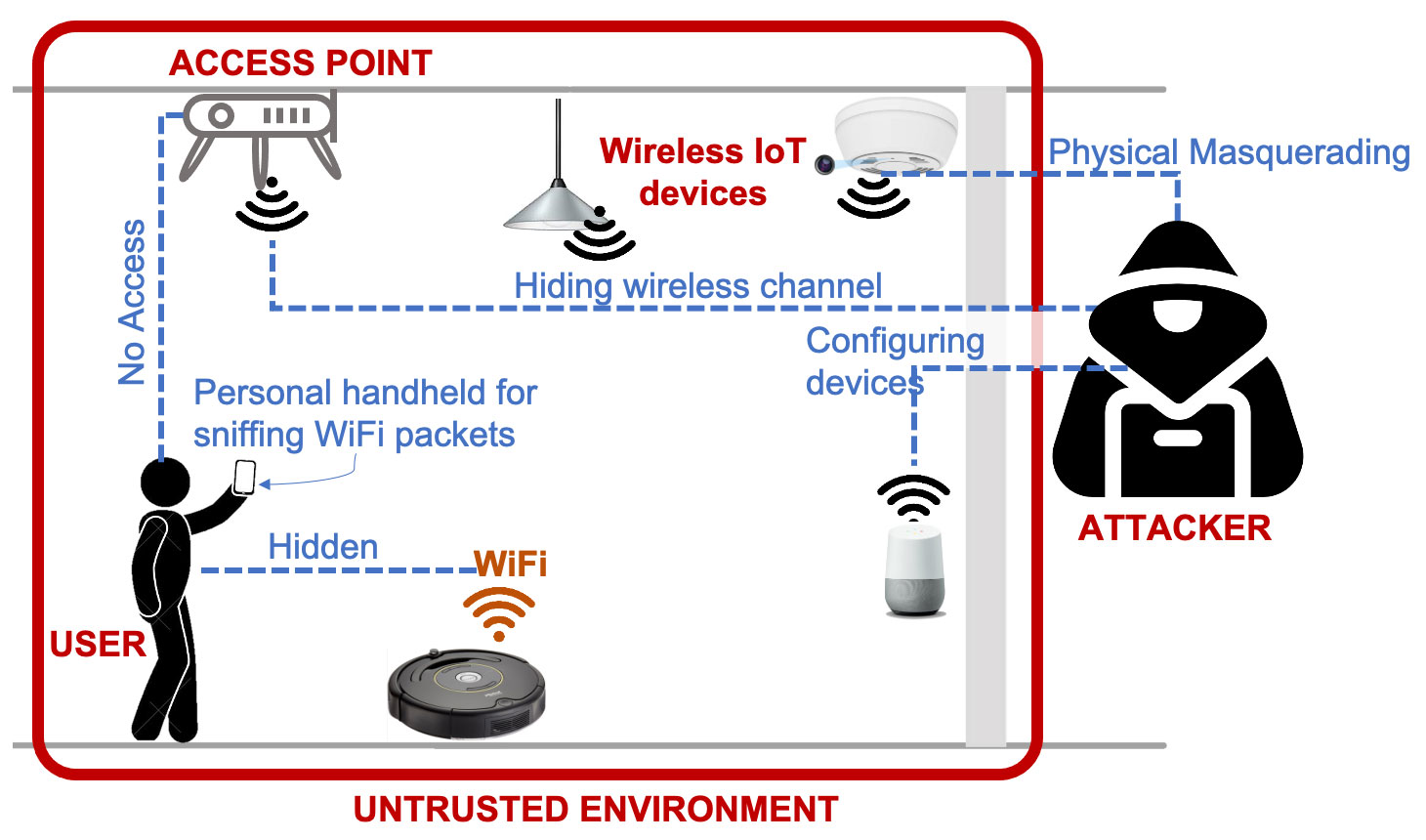
How to find hidden Wi-Fi devices in an untrusted environment using your phone] Source
Next, the researchers applied the technology that determines the type of device by its behavior. A simple example: a smart light switch might access the server once a minute and not show itself in any other way, while a webcam transmits streams of data and does so continuously. Using more than 50 such features and machine learning, the authors of the paper created “digital fingerprints” of typical IoT devices.
As a result, there’s no need to maintain and constantly update a database of suspicious devices in the app — Lumos will likely spot a Wi-Fi camera in your room by its characteristic behavior when transferring data, even if it has not seen the particular model before.

Another example from the Lumos demo video: finding a smart speaker. Source
Searching for IoT devices in augmented reality
The most eye-catching part of the study is the information superimposed over the image from the smartphone camera. Lumos uses AR technology to embed virtual objects in the image of the real environment sent to the phone’s display from the camera.
The approximate coordinates of located devices were overlaid on the image from the phone’s camera on an Apple smartphone using the standard ARKit library. This library uses various sensors of the phone to create a 3D model of the room. Along the way, the location of hidden connected devices is also determined.
For this, the researchers used another feature of the Wi-Fi module: the continuous measuring of signal strength from both the nearest access point and other wireless modules. Hence, by walking around the premises, measuring the signal level at different points, and performing some not overly complicated calculations, the app can determine the position of hidden devices in the room.

Indoor Wi-Fi device search map based on signal strength. Source
Implementation difficulties
We must stress again that this is scientific research — not the development of a commercial product; the authors are not trying to sell us anything. So it’s all the more interesting that they’ve put together a full-fledged spy-device detection system, rather than just show a part of it and leave the reader to fill in the blanks.
And the results are quite encouraging:
- The accuracy of determining device type was 95–98%. The chance of error is small.
- The location of IoT devices is determined with an accuracy of 1.5 meters — narrowing down the search area enough to find a hidden camera visually.
- The time it takes to discover nearby IoT devices is 30 minutes. For 27 of these minutes, the smartphone just lies there collecting data packets sent by surrounding devices. For the remaining three, the user has to walk around the room to determine the coordinates of the detected transmitters.
This means that the system really may help uncover unpleasant surprises in rented accommodation or in a hotel. But there are limitations. We’ve already noted the inability of a regular smartphone to scan the entirety of Wi-Fi traffic. It’s unlikely that manufacturers will do anything about this any time soon.
In addition, there are now lots of Wi-Fi devices in every home, and radio waves are quite good at passing through walls, especially if those aren’t made of reinforced concrete. This means you might accidentally find a camera installed in the neighbors’ place, or even on the outer wall of the building — and then falsely accuse the landlord of spying.
And then, of course, attempts to detect a hidden camera are futile if the apartment owner/cybercriminal uses a wired connection or records the footage in the old-fashioned way to a flash drive.
All this means that we’re unlikely to see commercial implementation of Lumos in the foreseeable future. It’s too “hackerish” for that — any commercial company that took on the development would face a mountain of issues and complaints, both from users (a camera was there, but wasn’t detected) and property owners (a camera wasn’t there, but the app said otherwise).
If it does get developed, it’d most likely be a plaything for techies. It may even be necessary to buy a specially modified smartphone for it. However, should this less-than-ideal scenario arise, the system may well be free (not counting the price of this special smartphone), since the authors of the paper promise to make the prototype source code freely available.