Jamf CIO: Apple will be the No. 1 enterprise endpoint by 2030

Credit to Author: Jonny Evans| Date: Thu, 16 Jun 2022 04:02:00 -0700
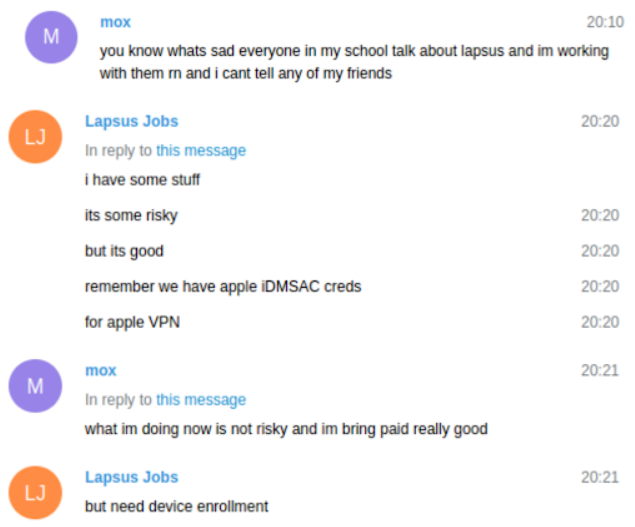
I spoke with Jamf CIO Linh Lam on a recent UK visit to mark the company’s 20th anniversary. The 2020 Bay Area CIO of the Year Finalist joined Jamf in 2021 – and thinks Apple will be the top enterprise endpoint by 2030 as its current momentum accelerates.
The changing landscape of enterprise IT
“The way the demand is growing and the expectations of younger generations joining the workforce, Apple devices will be the number one endpoint by 2030,” she told me.